

HAB boot的启动流程与实现步骤
电子说
描述
问题简介
在《深扒HAB boot 启动安全性》中,小编介绍了HAB boot的启动流程(如图1所示),其中的1、2、3验证步骤本质上就是验签过程。
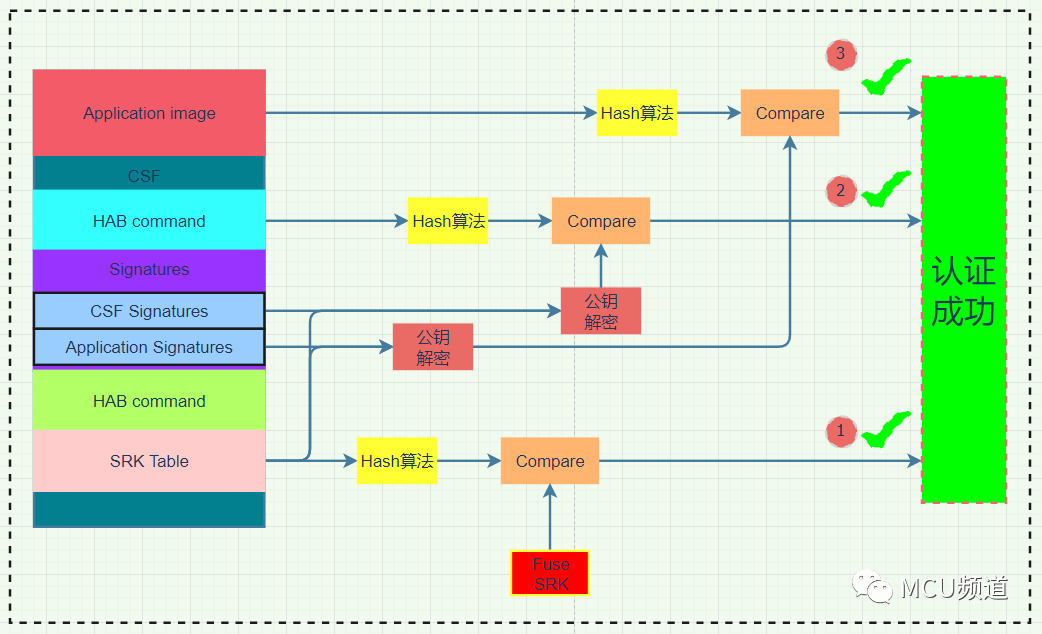 图1
图1验签过程在公钥可信的情况下,可用于检测数据的完整性(Integrity),身份认证(Authentication)和不可否认(Non-repudiation/Undeniable),而hab4_pki_tree.sh和hab4_pki_tree.bat脚本又保证生成的公钥与私钥对,证书是可信的,所以能“完美闭环”,使得HAB boot的安全性得到保证。
在应用手册AN12079中,介绍了实现HAB boot的步骤,大致可分为:
- 生成证书与密钥
- 对bootable image进行签名
- 打包签名后的bootable image生成SB文件
签名过程需借助elftosb工具和BD文件,其中BD文件包含了实现签名的命令,
options {
flags = 0x08;
startAddress = 0x60000000;
ivtOffset = 0x1000;
initialLoadSize = 0x2000;
entryPointAddress = 0x60004645;
}
sources {
elfFile = extern(0);
}
constants {
SEC_CSF_HEADER = 20;
SEC_CSF_INSTALL_SRK = 21;
SEC_CSF_INSTALL_CSFK = 22;
SEC_CSF_INSTALL_NOCAK = 23;
SEC_CSF_AUTHENTICATE_CSF = 24;
SEC_CSF_INSTALL_KEY = 25;
SEC_CSF_AUTHENTICATE_DATA = 26;
SEC_CSF_INSTALL_SECRET_KEY = 27;
SEC_CSF_DECRYPT_DATA = 28;
SEC_NOP = 29;
SEC_SET_MID = 30;
SEC_SET_ENGINE = 31;
SEC_INIT = 32;
SEC_UNLOCK = 33;
}
section (SEC_CSF_HEADER;
Header_Version="4.2",
Header_HashAlgorithm="sha256",
Header_Engine="DCP",
Header_EngineConfiguration=0,
Header_CertificateFormat="x509",
Header_SignatureFormat="CMS"
)
{
}
section (SEC_CSF_INSTALL_SRK;
InstallSRK_Table="............Users
xa07025secure_provisioning000000000000000000000000000gen_hab_certsSRK_hash.bin",
InstallSRK_SourceIndex=0
)
{
}
section (SEC_CSF_INSTALL_CSFK;
InstallCSFK_File="............Users
xa07025secure_provisioning000000000000000000000000000crtsCSF1_1_sha256_2048_65537_v3_usr_crt.pem",
InstallCSFK_CertificateFormat="x509"
)
{
}
section (SEC_CSF_AUTHENTICATE_CSF)
{
}
section (SEC_CSF_INSTALL_KEY;
InstallKey_File="............Users
xa07025secure_provisioning000000000000000000000000000crtsIMG1_1_sha256_2048_65537_v3_usr_crt.pem",
InstallKey_VerificationIndex=0,
InstallKey_TargetIndex=2)
{
}
section (SEC_CSF_AUTHENTICATE_DATA;
AuthenticateData_VerificationIndex=2,
AuthenticateData_Engine="DCP",
AuthenticateData_EngineConfiguration=0)
{
}
section (SEC_SET_ENGINE;
SetEngine_HashAlgorithm = "sha256",
SetEngine_Engine = "DCP",
SetEngine_EngineConfiguration = "0")
{
}
section (SEC_UNLOCK;
Unlock_Engine = "SNVS",
Unlock_features = "ZMK WRITE"
)
{
}
在运行类似下面的命令后,bootable image的组成会有如图2所示的变化。
./elftosb.exe -f imx -V -c imx-flexspinor-normal-signed.bd -o ivt_application_signed.bin led_demo_evk_flexspi_nor_0x60002000.srec
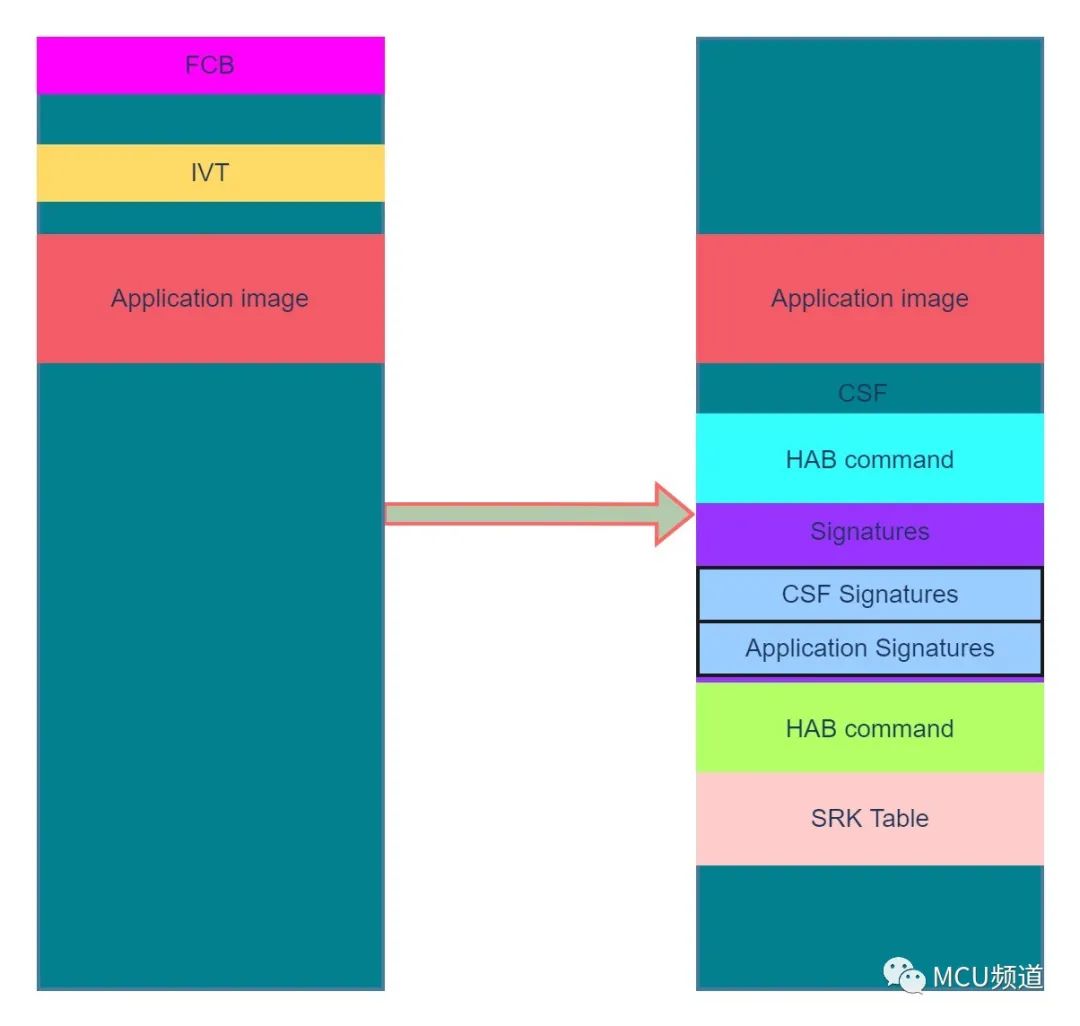 图2
图2在仔细查看BD文件后,我们会发现里面有加载SRK公钥,IMG1和CSF1证书等命令,却没有了关于私钥的相关命令?那么私钥是如何参与bootable image的签名过程的呢?
私钥在哪里?
图3的左边部分表示elftosb.exe执行如下命令后,首先application和CSF(Command Sequence File)会进行Hash运算生成摘要,跟着私钥会对其加密生成签名。
./elftosb.exe -f imx -V -c imx-flexspinor-normal-signed.bd -o ivt_application_signed.bin led_demo_evk_flexspi_nor_0x60002000.srec
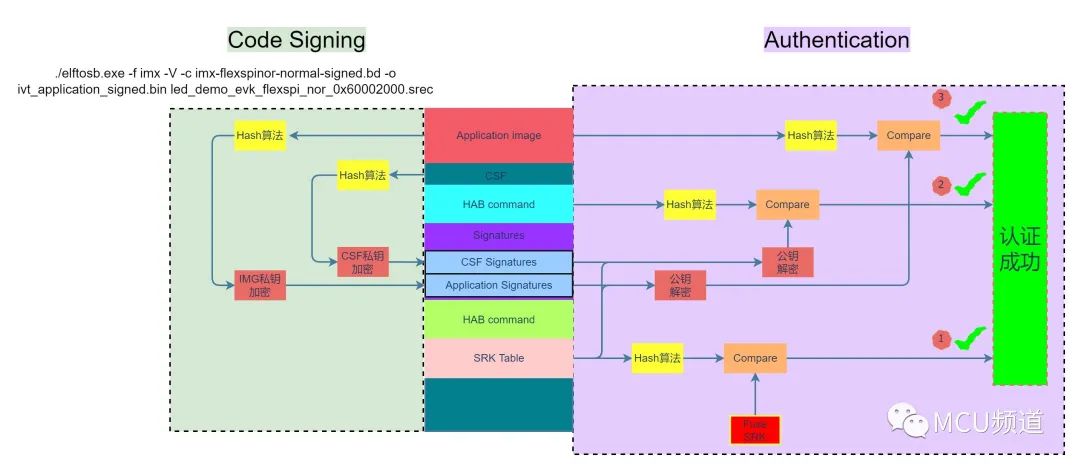 图3
图3
那么elftosb.exe是从哪里加载私钥的呢?答案就是在与证书所处文件夹crts同一层目录下的keys文件夹中,且elftosb.exe会加载与BD文件中的公钥证书所对应的私钥文件,比如上述BD文件的公钥证书是CSF1_1_sha256_2048_65537_v3_usr_crt.pem和IMG1_1_sha256_2048_65537_v3_usr_crt.pem,那么对应的私钥文件就是CSF1_1_sha256_2048_65537_v3_usr_key.pem和IMG1_1_sha256_2048_65537_v3_usr_key.pem,当然,你也可以移除keys文件夹来进行验证。
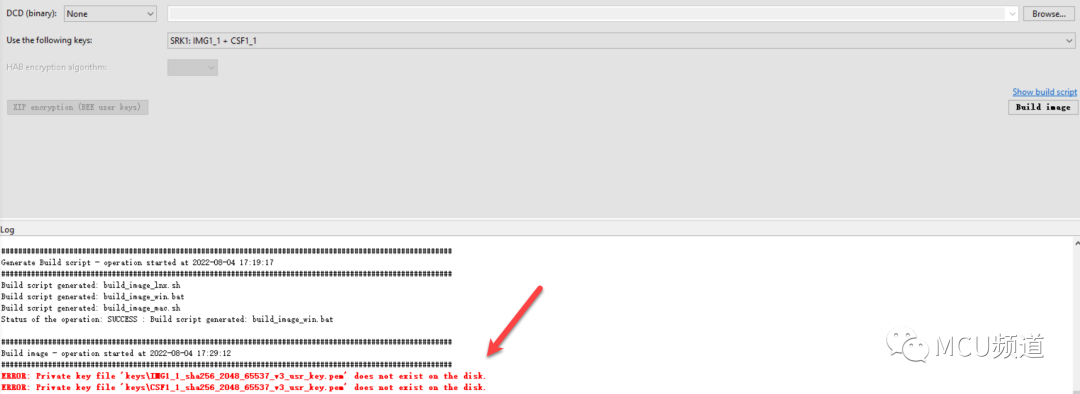 图4
图4
-
u-boot启动流程分析2023-07-12 1470
-
U-BOOT的启动流程分享2022-01-18 1266
-
U-boot的完整启动流程是怎样的?2022-03-03 1335
-
为什么U-boot显示的HAB事件数据不符合HAB的数据表?2023-03-16 308
-
i.MX8M Mini安全启动HAB错误怎么解决?2023-03-28 716
-
IMX8M没有HAB事件,而SRK_HASH未定义是为什么?2023-04-03 480
-
如何在imx6q实现HAB?2023-04-04 489
-
imx6q安全启动HAB错误的原因?2023-04-06 602
-
嵌入式U-BOOT的启动流程及移植2011-02-25 825
-
串行SPI Nor Flash启动流程2018-03-16 22711
-
AURIX™ TC3xx启动流程详解2023-06-06 5224
-
Spring Boot启动 Eureka流程2023-10-10 1525
-
安全启动Secure Boot流程2023-11-02 3096
-
冷启动(Cold boot)流程及阶段划分2023-11-07 4885
-
springboot启动流程2023-11-22 1183
全部0条评论

快来发表一下你的评论吧 !

