

怎样通过IPsec野蛮模式实现分支之间相互通信呢
电子说
1.4w人已加入
描述
一、组网及说明
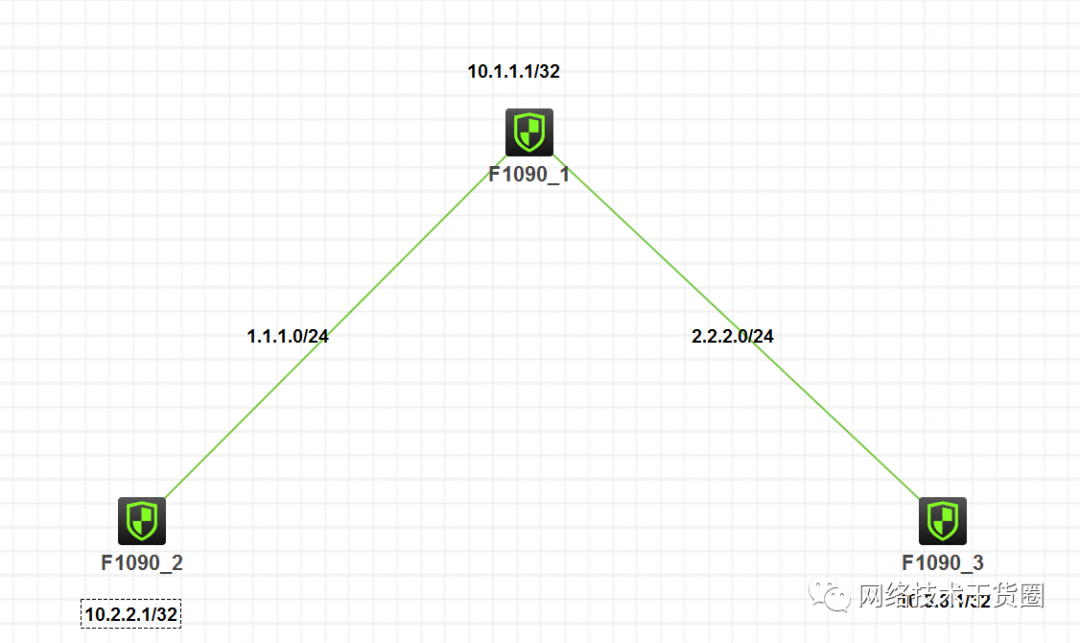
注:如无特别说明,描述中的 FW1 或 MSR1 对应拓扑中设备名称末尾数字为 1 的设备,FW2 或 MSR2 对应拓扑中设备名称末尾数字为 2 的设备,以此类推;另外,同一网段中,IP 地址的主机位为其设备编号,如 FW1 的 g0/0 接口若在 1.1.1.0/24 网段,则其 IP 地址为 1.1.1.1/24,以此类推。
二、实验需求
FW1代表中心节点,FW2和FW3代表分支。
FW上使用环回口Loopback0模拟业务网段。
分支分别和中心节点通信,各分支节点之间可以相互通信。
三、配置步骤
3.1 IP、路由、安全域
FW1
# interface LoopBack0 ip address 10.1.1.1 255.255.255.255 # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 2.2.2.1 255.255.255.0 ipsec apply policy ply # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/0 import interface GigabitEthernet1/0/1 # ip route-static 10.2.2.1 32 1.1.1.2 ip route-static 10.3.3.1 32 2.2.2.3 # security-policy ip rule 0 name any action pass
FW2
# interface LoopBack0 ip address 10.2.2.1 255.255.255.255 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 1.1.1.2 255.255.255.0 ipsec apply policy ply # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/0 import interface GigabitEthernet1/0/1 # ip route-static 0.0.0.0 0 1.1.1.1 # security-policy ip rule 0 name any action pass
FW3
# interface LoopBack0 ip address 10.3.3.1 255.255.255.0 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 2.2.2.3 255.255.255.0 ipsec apply policy ply # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/0 import interface GigabitEthernet1/0/1 # ip route-static 0.0.0.0 0 2.2.2.1 # security-policy ip rule 0 name any action pass #
3.2 IKE部分
FW1
# ike keychain k1 pre-shared-key hostname f2 key cipher $c$3$rFTHo6O4pPLOHvZEwmSFGc3gjFRY7Q75Qw== # ike keychain k2 pre-shared-key hostname f3 key cipher $c$3$lo0leXtmx41UHB7Vxok9kFeOJxZnJZ0miw== # ike profile pf keychain k1 keychain k2 dpd interval 10 on-demand exchange-mode aggressive local-identity fqdn f1 match remote identity fqdn f2 match remote identity fqdn f3
FW2
# ike keychain k1 pre-shared-key address 1.1.1.1 255.255.255.255 key cipher $c$3$v44JHWonfkj3w9BqDNkQ+LEIFRiUlBKUgw== # ike profile pf keychain k1 exchange-mode aggressive local-identity fqdn f2 match remote identity fqdn f1
FW3
# ike keychain k1 pre-shared-key address 2.2.2.1 255.255.255.255 key cipher $c$3$PKsnAPnnOgZicN73gXZd3L3ZO9OR3IuS1A== # ike profile pf keychain k1 exchange-mode aggressive local-identity fqdn f3 match remote identity fqdn f1
3.3 IPsec部分
FW1
# acl advanced 3000 rule 0 permit ip source 10.1.1.1 0 destination 10.2.2.1 0 rule 5 permit ip source 10.1.1.1 0 destination 10.3.3.1 0 rule 10 permit ip source 10.3.3.1 0 destination 10.2.2.1 0 rule 15 permit ip source 10.2.2.1 0 destination 10.3.3.1 0 # ipsec transform-set ts esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # ipsec policy-template pt 1 transform-set ts security acl 3000 ike-profile pf # ipsec policy ply 1 isakmp template pt
FW2
# acl advanced 3000 rule 0 permit ip source 10.2.2.1 0 destination 10.1.1.1 0 rule 5 permit ip source 10.2.2.1 0 destination 10.3.3.1 0 # ipsec transform-set ts esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # ipsec policy ply 1 isakmp transform-set ts security acl 3000 remote-address 1.1.1.1 ike-profile pf
FW3
# acl advanced 3000 rule 0 permit ip source 10.3.3.1 0 destination 10.1.1.1 0 rule 5 permit ip source 10.3.3.1 0 destination 10.2.2.1 0 # ipsec transform-set ts esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # ipsec policy ply 1 isakmp transform-set ts security acl 3000 remote-address 2.2.2.1 ike-profile pf
四、配置关键点
分支和中心节点之间的隧道建立要通过分支来触发,即FW2向FW1发起访问,FW3向FW1发起访问。
分支和分支之间建立隧道需要两边触发,即FW2向FW3发起访问,FW3向FW2发起访问。
分支的感兴趣流除了目的是中心节点外,还需要包括到分支的。
FW1上的ipsec sa如下:
------------------------------- Interface: GigabitEthernet1/0/0 ------------------------------- ----------------------------- IPsec policy: ply Sequence number: 1 Mode: Template ----------------------------- Tunnel id: 1 Encapsulation mode: tunnel Perfect Forward Secrecy: Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Transmitting entity: Responder Path MTU: 1444 Tunnel: local address: 1.1.1.1 remote address: 1.1.1.2 Flow: sour addr: 10.1.1.1/255.255.255.255 port: 0 protocol: ip dest addr: 10.2.2.1/255.255.255.255 port: 0 protocol: ip [Inbound ESP SAs] SPI: 3754823141 (0xdfce0de5) Connection ID: 4294967298 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3562 Max received sequence-number: 4 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 1056998950 (0x3f008626) Connection ID: 4294967299 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3562 Max sent sequence-number: 4 UDP encapsulation used for NAT traversal: N Status: Active ----------------------------- IPsec policy: ply Sequence number: 1 Mode: Template ----------------------------- Tunnel id: 2 Encapsulation mode: tunnel Perfect Forward Secrecy: Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Transmitting entity: Responder Path MTU: 1444 Tunnel: local address: 1.1.1.1 remote address: 1.1.1.2 Flow: sour addr: 10.3.3.1/255.255.255.255 port: 0 protocol: ip dest addr: 10.2.2.1/255.255.255.255 port: 0 protocol: ip [Inbound ESP SAs] SPI: 3260450656 (0xc2568760) Connection ID: 4294967300 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3575 Max received sequence-number: 8 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 2013923382 (0x780a0836) Connection ID: 4294967301 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3575 Max sent sequence-number: 5 UDP encapsulation used for NAT traversal: N Status: Active ------------------------------- Interface: GigabitEthernet1/0/1 ------------------------------- ----------------------------- IPsec policy: ply Sequence number: 1 Mode: Template ----------------------------- Tunnel id: 0 Encapsulation mode: tunnel Perfect Forward Secrecy: Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Transmitting entity: Responder Path MTU: 1444 Tunnel: local address: 2.2.2.1 remote address: 2.2.2.3 Flow: sour addr: 10.1.1.1/255.255.255.255 port: 0 protocol: ip dest addr: 10.3.3.1/255.255.255.255 port: 0 protocol: ip [Inbound ESP SAs] SPI: 2022161426 (0x7887bc12) Connection ID: 4294967296 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3554 Max received sequence-number: 4 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 3633752750 (0xd896aaae) Connection ID: 4294967297 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3554 Max sent sequence-number: 4 UDP encapsulation used for NAT traversal: N Status: Active ----------------------------- IPsec policy: ply Sequence number: 1 Mode: Template ----------------------------- Tunnel id: 3 Encapsulation mode: tunnel Perfect Forward Secrecy: Inside VPN: Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Transmitting entity: Responder Path MTU: 1444 Tunnel: local address: 2.2.2.1 remote address: 2.2.2.3 Flow: sour addr: 10.2.2.1/255.255.255.255 port: 0 protocol: ip dest addr: 10.3.3.1/255.255.255.255 port: 0 protocol: ip [Inbound ESP SAs] SPI: 3168528224 (0xbcdbe760) Connection ID: 4294967302 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3583 Max received sequence-number: 5 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for NAT traversal: N Status: Active [Outbound ESP SAs] SPI: 2761355159 (0xa496ef97) Connection ID: 4294967303 Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3583 Max sent sequence-number: 5 UDP encapsulation used for NAT traversal: N Status: Active
实验结束!
审核编辑:刘清
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
两块esp32-c3如何实现蓝牙相互通信?2024-06-11 804
-
IR915和IR615建立IPsec VPN实现子网互通2024-07-24 457
-
急求C8051F340实现单片机与pc机之间简单的相互通信的串口通信2012-06-19 2382
-
更改wifi信号频率实现有且只有2个设备相互通信,避免干扰2016-06-23 5597
-
进程的相互通信2019-08-07 1387
-
请问如何通过stm32f103的u***与计算机实现相互通信?2020-04-09 3651
-
请问NRF24L01能否实现多机相互通信?2020-05-15 2515
-
怎样通过USART来实现单片机和电脑之间的通信呢2021-12-10 1544
-
NRF24L01模块是否可以一对多进行相互通信呢2021-12-16 3564
-
ESP8266无线模块之间是如何进行相互通信的2022-01-18 1706
-
如何通过HAL库实现STM32F103C8T6两块板之间的IIC主从相互通信2022-02-14 676
-
用一个芯片上的两个SPI接口相互通信实现2022-02-17 2075
-
如何实现两个ESP8266相互通信呢2022-02-22 2068
-
2个esp8266 WiFi模块之间的相互通信2023-09-25 1116
-
KUKA机箱内部安全组件之间通过EtherCAT和FSoE相互通讯2020-06-28 5564
全部0条评论

快来发表一下你的评论吧 !

