

为什么防火墙默认就可以访问任何区域?
安全设备/系统
描述
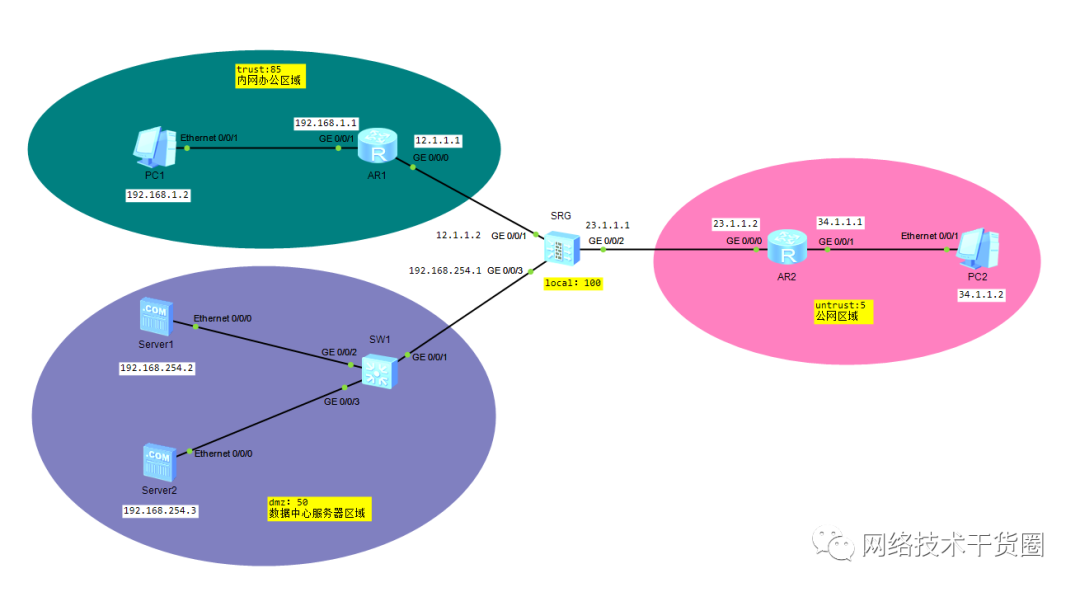
实验拓扑
防火墙的工作模式
透明网桥模式:可以理解成二层交换机,对三层的IP、路由没有任何影响。透明模式仍然可以抵御外部入侵,但是不能发挥防火墙的全部功能
例如下图:前期IP地址都已经规划好了,组网都已经结束了。突然领导说要加个防火墙,那基本就用透明模式。
路由模式:可以理解成三层路由器
防火墙的区域(zone)
防火墙默认区域的介绍
优先级代表着可信程度,优先级越高表示越信任,即数字越大越信任
[SRG]dis zone 2249 2020/11/18 local #本地区域 priority is 100 #默认优先级100 # trust #内网用户 priority is 85 #默认优先级85 interface of the zone is (1): GigabitEthernet0/0/0 # untrust #外网用户 priority is 5 #默认优先级5 interface of the zone is (0): # dmz #dmz区域 priority is 50 #默认优先级50 interface of the zone is (0): #
接下来我们按照拓扑把防火墙的端口划分到相应的区域。
[SRG]firewall zone ? dmz Indicate the DMZ local Indicate the Local zone name Indicate the security zone name trust Indicate the Trust zone untrust Indicate the Untrust zone vpn-instance Indicate VPN instance [SRG]firewall zone trust [SRG-zone-trust]add interface g0/0/1 [SRG-zone-trust]q [SRG]firewall zone dmz [SRG-zone-dmz]add int g0/0/3 [SRG-zone-dmz]q [SRG]firewall zone untrust [SRG-zone-untrust]add interface g0/0/2 [SRG-zone-untrust]q
接口只有划分了区域才可以使用。
这样做完之后,只有trust区域才能访问防火墙。内网也不能访问外网。
[R1]ip route-static 0.0.0.0 0 12.1.1.2
[R2]ip route-static 0.0.0.0 0 23.1.1.1 #这里应该用nat地址转换的,但我们还没有接触到防火墙nat转换,所以先用静态路由代替,本篇后面会讲到。
[SRG]ip route-static 0.0.0.0 0 23.1.1.2 #到外网的路由 [SRG]ip route-static 192.168.1.0 24 12.1.1.1 #到内网的路由
虽然我们加入了2条路由,但是由于还没有配置策略,所以内网用户还是不能访问外网。
防火墙策略概念
防火墙策略的方向
outbound:高优先级访问低优先级
inbound:低优先级访问高优先级
注意:“访问”仅指的是出包即主动发起的第一个报文,即建立会话(session)的过程。
默认高优先级可以访问低优先级,但是低优先级无法回包,相当于回执路由回不来。所以无法ping通。但是我的确是访问了,防火墙就会记录这一条信息。
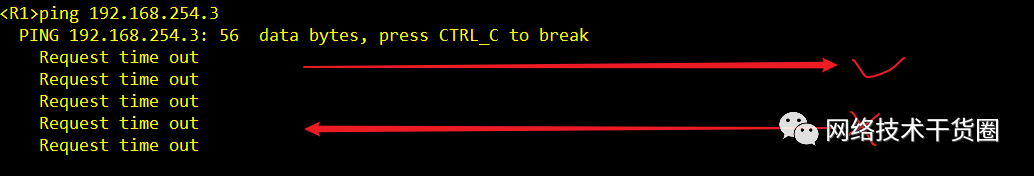
防火墙默认可以访问任何一个区域
ping 192.168.254.2 2306 2020/11/18 PING 192.168.254.2: 56 data bytes, press CTRL_C to break Reply from 192.168.254.2: bytes=56 Sequence=1 ttl=255 time=220 ms Reply from 192.168.254.2: bytes=56 Sequence=2 ttl=255 time=50 ms Reply from 192.168.254.2: bytes=56 Sequence=3 ttl=255 time=170 ms Reply from 192.168.254.2: bytes=56 Sequence=4 ttl=255 time=100 ms Reply from 192.168.254.2: bytes=56 Sequence=5 ttl=255 time=140 ms --- 192.168.254.2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 50/136/220 ms from wljsghq ping 192.168.1.2 2314 2020/11/18 PING 192.168.1.2: 56 data bytes, press CTRL_C to break Request time out Reply from 192.168.1.2: bytes=56 Sequence=2 ttl=127 time=80 ms Reply from 192.168.1.2: bytes=56 Sequence=3 ttl=127 time=80 ms Reply from 192.168.1.2: bytes=56 Sequence=4 ttl=127 time=80 ms Reply from 192.168.1.2: bytes=56 Sequence=5 ttl=127 time=270 ms --- 192.168.1.2 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 80/127/270 ms ping 23.1.1.2 2328 2020/11/18 PING 23.1.1.2: 56 data bytes, press CTRL_C to break Reply from 23.1.1.2: bytes=56 Sequence=1 ttl=255 time=160 ms Reply from 23.1.1.2: bytes=56 Sequence=2 ttl=255 time=70 ms Reply from 23.1.1.2: bytes=56 Sequence=3 ttl=255 time=70 ms Reply from 23.1.1.2: bytes=56 Sequence=4 ttl=255 time=90 ms Reply from 23.1.1.2: bytes=56 Sequence=5 ttl=255 time=110 ms --- 23.1.1.2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 70/100/160 ms ping 34.1.1.2 2338 2020/11/18 PING 34.1.1.2: 56 data bytes, press CTRL_C to break Request time out Reply from 34.1.1.2: bytes=56 Sequence=2 ttl=127 time=80 ms Reply from 34.1.1.2: bytes=56 Sequence=3 ttl=127 time=100 ms Reply from 34.1.1.2: bytes=56 Sequence=4 ttl=127 time=80 ms Reply from 34.1.1.2: bytes=56 Sequence=5 ttl=127 time=220 ms --- 34.1.1.2 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 80/120/220 ms
为什么防火墙默认就可以访问任何区域呢?这是和防火墙的默认策略有关。
防火墙的默认策略
dis cu ... firewall packet-filter default permit interzone local trust direction inbound #permit允许,local本地区域,trust内网区域,inbound:优先级由低——>高 上面的意思就是:local本地区域,trust内网区域,这两个区域默认允许低——>高 firewall packet-filter default permit interzone local trust direction outbound 上面的意思就是:local本地区域,trust内网区域,这两个区域默认允许高——>低 firewall packet-filter default permit interzone local untrust direction outboun 上面的意思就是:local本地区域,untrust外网区域,这两个区域默认允许高——>低 ...
三条默认策略组合起来意思就是:
默认防火墙和内网区域允许进和出,即相互通信;
防火墙和外网区域之间,只能出,不能进。即防火墙可以ping通外网,外网无法ping通防火墙;
同样防火墙访问DMZ也是只能出,不能进。即防火墙可以ping通DMZ的server,但server无法ping通防火墙。
防火墙的策略配置
1、内网用户访问外网
[SRG]firewall packet-filter default permit interzone trust untrust direction out bound 2321 2020/11/18 Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Ar e you sure you want to continue?[Y/N]y [R1]ping 23.1.1.2 #R1 ping R2 PING 23.1.1.2: 56 data bytes, press CTRL_C to break Reply from 23.1.1.2: bytes=56 Sequence=1 ttl=254 time=50 ms Reply from 23.1.1.2: bytes=56 Sequence=2 ttl=254 time=50 ms Reply from 23.1.1.2: bytes=56 Sequence=3 ttl=254 time=30 ms Reply from 23.1.1.2: bytes=56 Sequence=4 ttl=254 time=30 ms Reply from 23.1.1.2: bytes=56 Sequence=5 ttl=254 time=40 ms PC>ping 34.1.1.2 #pc1 PING pc2 Ping 34.1.1.2: 32 data bytes, Press Ctrl_C to break Request timeout! From 34.1.1.2: bytes=32 seq=2 ttl=125 time=62 ms From 34.1.1.2: bytes=32 seq=3 ttl=125 time=63 ms From 34.1.1.2: bytes=32 seq=4 ttl=125 time=31 ms From 34.1.1.2: bytes=32 seq=5 ttl=125 time=31 ms --- 34.1.1.2 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/46/63 ms PC>
2、内网用户访问DMZ区域的服务器
[SRG]firewall packet-filter default permit interzone trust dmz direction outboun d 2300 2020/11/18 Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Ar e you sure you want to continue?[Y/N]y PC>ping 34.1.1.2 Ping 34.1.1.2: 32 data bytes, Press Ctrl_C to break Request timeout! From 34.1.1.2: bytes=32 seq=2 ttl=125 time=62 ms From 34.1.1.2: bytes=32 seq=3 ttl=125 time=63 ms From 34.1.1.2: bytes=32 seq=4 ttl=125 time=31 ms From 34.1.1.2: bytes=32 seq=5 ttl=125 time=31 ms --- 34.1.1.2 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/46/63 ms PC>
3、外网用户访问DMZ服务器
[SRG]firewall packet-filter default permit interzone untrust dmz direction inbou nd 0011 2020/11/19 Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Ar e you sure you want to continue?[Y/N]y [SRG] PC>ping 192.168.254.2 Ping 192.168.254.2: 32 data bytes, Press Ctrl_C to break From 192.168.254.2: bytes=32 seq=1 ttl=253 time=15 ms From 192.168.254.2: bytes=32 seq=2 ttl=253 time=63 ms From 192.168.254.2: bytes=32 seq=3 ttl=253 time=47 ms From 192.168.254.2: bytes=32 seq=4 ttl=253 time=31 ms From 192.168.254.2: bytes=32 seq=5 ttl=253 time=47 ms --- 192.168.254.2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 15/40/63 ms
防火墙上的NAT
防火墙上的NAT的基本配置
[R2]undo ip route-static 0.0.0.0 0 23.1.1.1 #删除之前R2上面的静态路由
[SRG]nat-policy interzone trust untrust outbound [SRG-nat-policy-interzone-trust-untrust-outbound]policy 1 #1策略ID [SRG-nat-policy-interzone-trust-untrust-outbound-1]action ? no-nat Indicate that no NAT action is configured source-nat Indicate that the source NAT action is configured [SRG-nat-policy-interzone-trust-untrust-outbound-1]action source-nat [SRG-nat-policy-interzone-trust-untrust-outbound-1]easy-ip g0/0/2
验证结果
PC>ping 34.1.1.2 Ping 34.1.1.2: 32 data bytes, Press Ctrl_C to break Request timeout! From 34.1.1.2: bytes=32 seq=2 ttl=125 time=32 ms From 34.1.1.2: bytes=32 seq=3 ttl=125 time=31 ms From 34.1.1.2: bytes=32 seq=4 ttl=125 time=62 ms From 34.1.1.2: bytes=32 seq=5 ttl=125 time=63 ms --- 34.1.1.2 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/47/63 ms
抓包看看
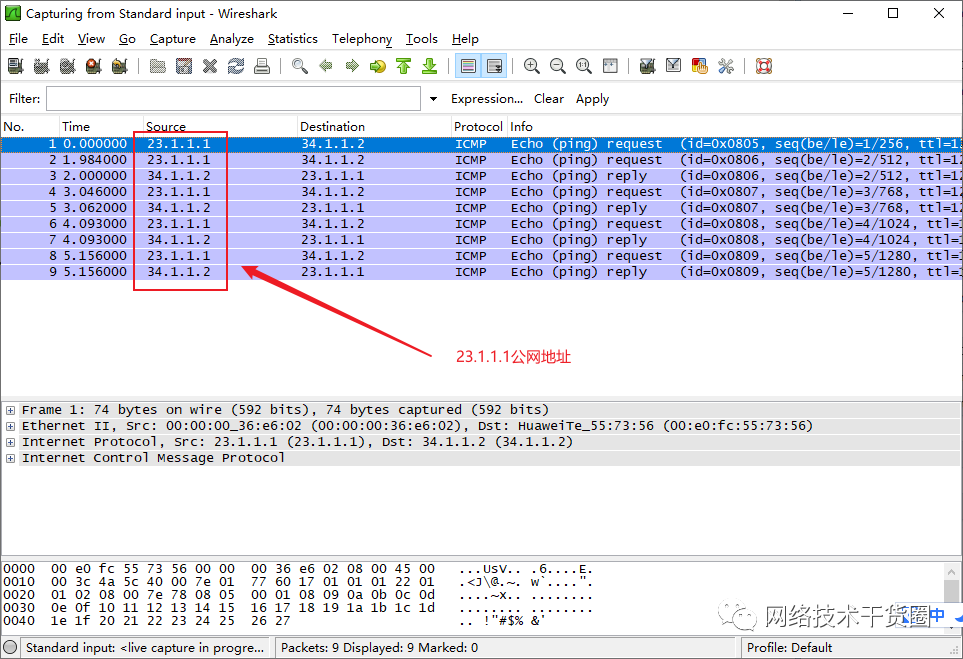
防火墙NAT端口映射
端口映射
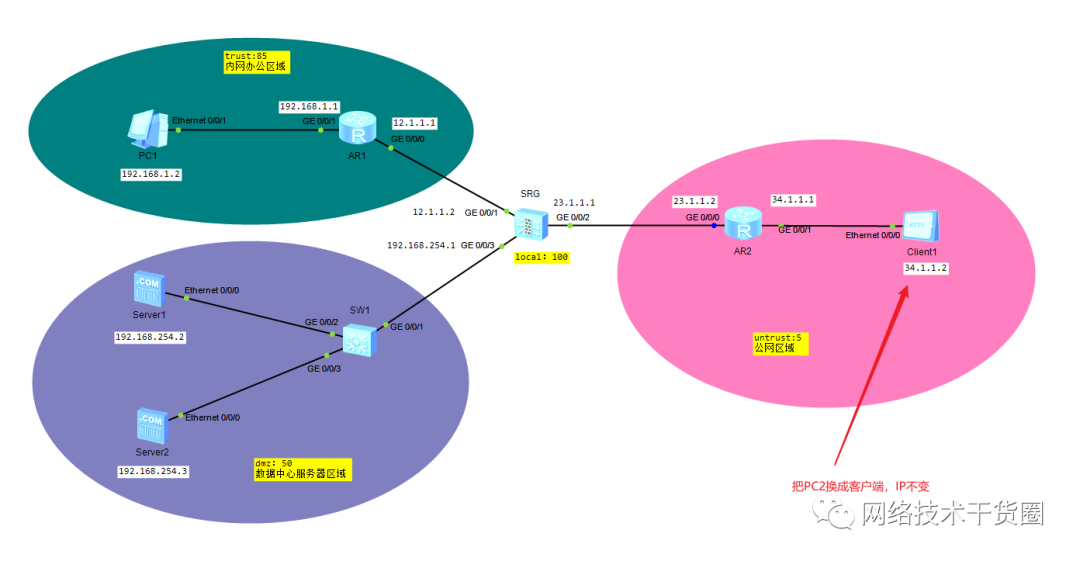
映射服务器server1的80端口到外网的23.1.1.3:80
[SRG]nat server protocol tcp global 23.1.1.3 80 inside 192.168.254.2 80
说明:外网IP有很多:23.1.1.0/24 整个段都可以用。
验证结果
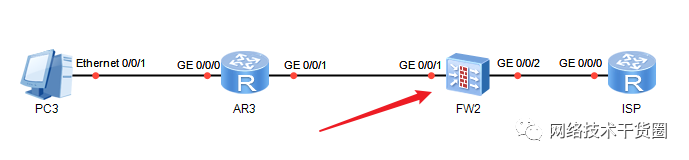
如果要验证,拓扑就需要更改一下,如下图:
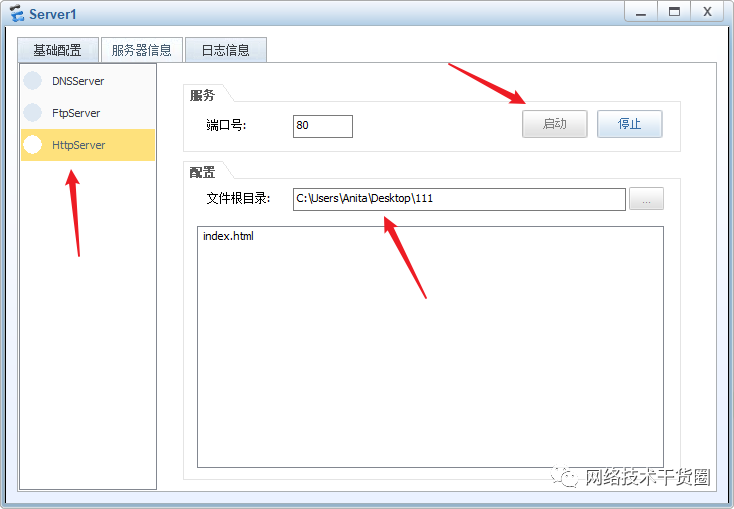
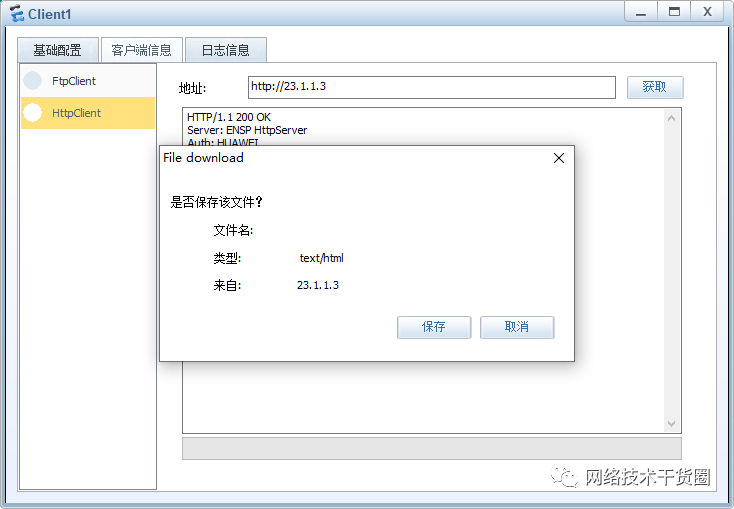
查看防火墙NAT转换表
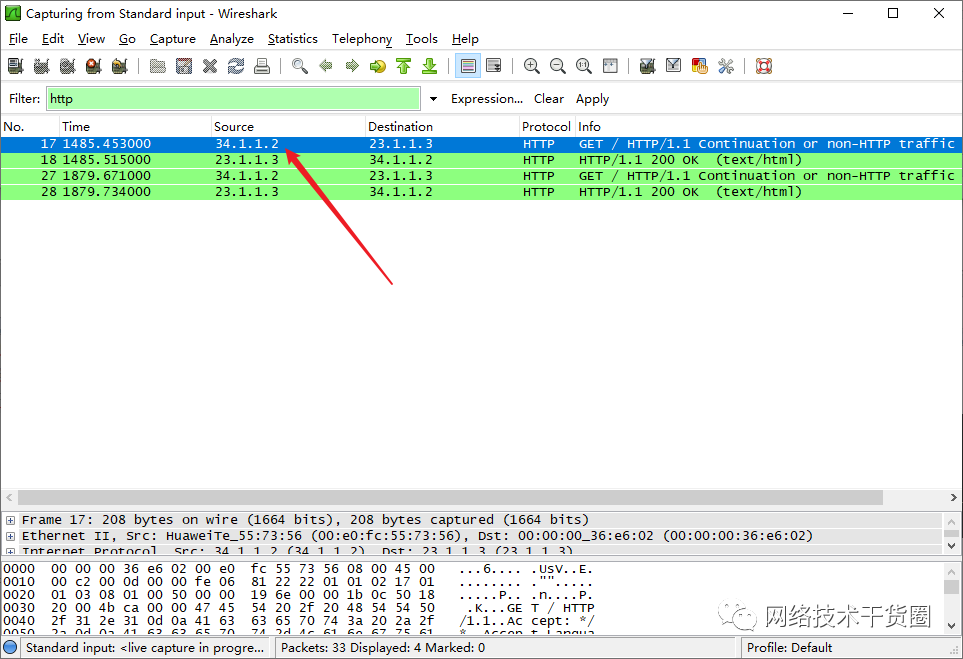
[SRG]display firewall session table nat 0016 2020/11/19 Current Total Sessions : 1 http VPN:public --> public 34.1.1.2:2050-->23.1.1.3:80[192.168.254.2:80] [SRG]
抓包看看
编辑:黄飞
-
【电脑安全技巧】电脑防火墙的使用技巧2013-07-12 0
-
Linux防火墙的配置方法(firewalld服务)2015-10-30 0
-
发现 STM32 防火墙的安全配置2018-07-27 0
-
防火墙技术2009-06-16 760
-
防火墙原理入门2009-08-01 1027
-
谈防火墙及防火墙的渗透技术2009-08-01 1065
-
IDS与防火墙对比2009-12-28 2034
-
防火墙管理2010-01-08 1346
-
防火墙的分类2010-01-08 6884
-
究竟什么是防火墙?2010-02-24 785
-
防火墙,防火墙的作用有哪些?2010-04-03 8339
-
Linux 防火墙配置基础篇2017-11-07 753
-
什么是防火墙?防火墙如何工作?2020-09-30 5389
-
什么是防火墙?防火墙的架构与工作方式?2022-12-13 1224
-
硬件防火墙和软件防火墙区别2024-10-21 137
全部0条评论

快来发表一下你的评论吧 !

