

如何破解JS加密?
描述
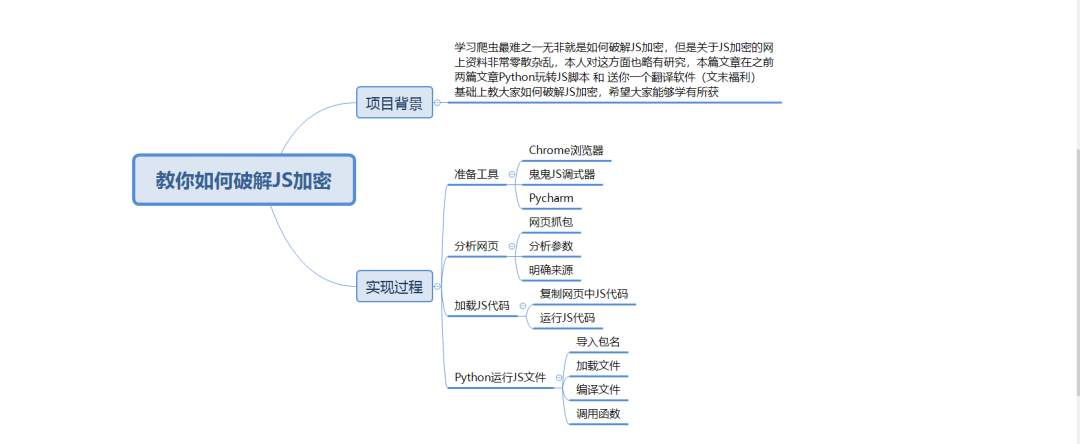
一.项目背景
学习爬虫最难之一无非就是如何破解JS加密,但是关于JS加密的网上资料非常零散杂乱,本人对这方面也略有研究,本篇文章在之前两篇文章[Python玩转JS脚本](http://mp.weixin.qq.com/s?__biz=MzIzODI4ODM2MA==&mid=2247486598&idx=1&sn=1fb3996f99d0080c0c146395bb1a5139&chksm=e93ae001de4d6917a52ce50472e95d8153f23dad2409046d78ec0627b4af8c3f894349b41db9&scene=21#wechat_redirect) 和 [送你一个翻译软件(文末福利)](http://mp.weixin.qq.com/s?__biz=MzIzODI4ODM2MA==&mid=2247485945&idx=1&sn=4d085a0fbf2825fb8ce9c1466fad34b4&chksm=e93ae57ede4d6c68476a422b0d0102d06acb269853150894579475269c2298ba39710fd835fe&scene=21#wechat_redirect) 基础上教大家如何破解JS加密,希望大家能够学有所获
二.实现过程
1.准备工具
》》Chrome浏览器
》》鬼鬼JS调试工具
》》Pycharm
如果没有鬼鬼JS调试器(可以写JS代码的编译器,运行时需要关闭杀毒软件)工具的小伙伴,后台发送" **JS"** 关键字即可获取。
2.分析网页
》》网页抓包
》》分析参数
》》明确来源
我们的目标网址是微博登录网址https://weibo.com/login.php,通过点击浏览器Network抓包找到真正的请求网络网址,通过查看请求信息发现是一个POST请求(一般来说POST请求要比GET请求安全的多)如下图所示。

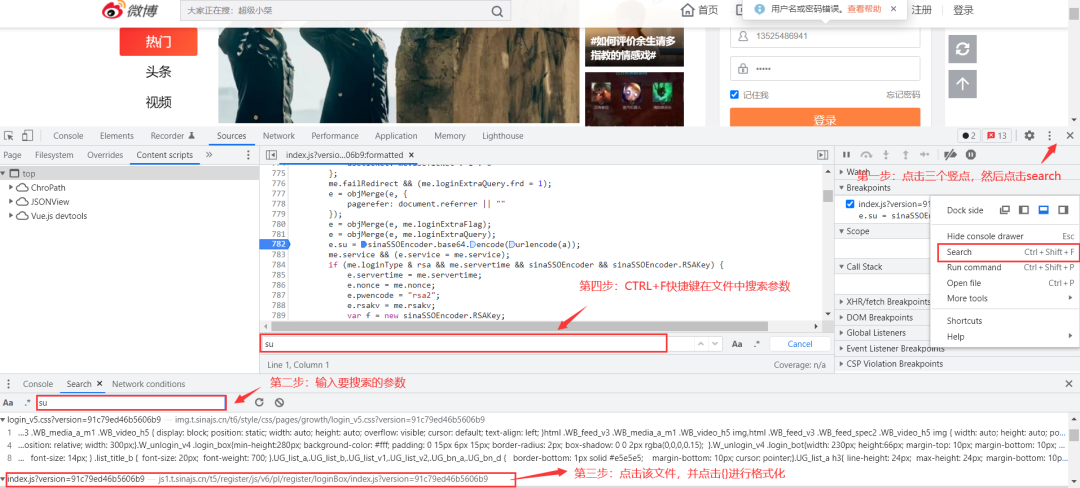
我们主要任务是如何破解请求参数 su (如下图所示),该参数明显是一个被加密的参数(关于其他参数比如s****p等参数破解方法都是一样的,感兴趣的读者可以下去试试,有问题的话可以后台私聊我)

接下来我们需要搜索我们要破解的参数,如下图所示(如果还有不清楚的请参考之前文章[)](http://mp.weixin.qq.com/s?__biz=MzIzODI4ODM2MA==&mid=2247485945&idx=1&sn=4d085a0fbf2825fb8ce9c1466fad34b4&chksm=e93ae57ede4d6c68476a422b0d0102d06acb269853150894579475269c2298ba39710fd835fe&scene=21#wechat_redirect)
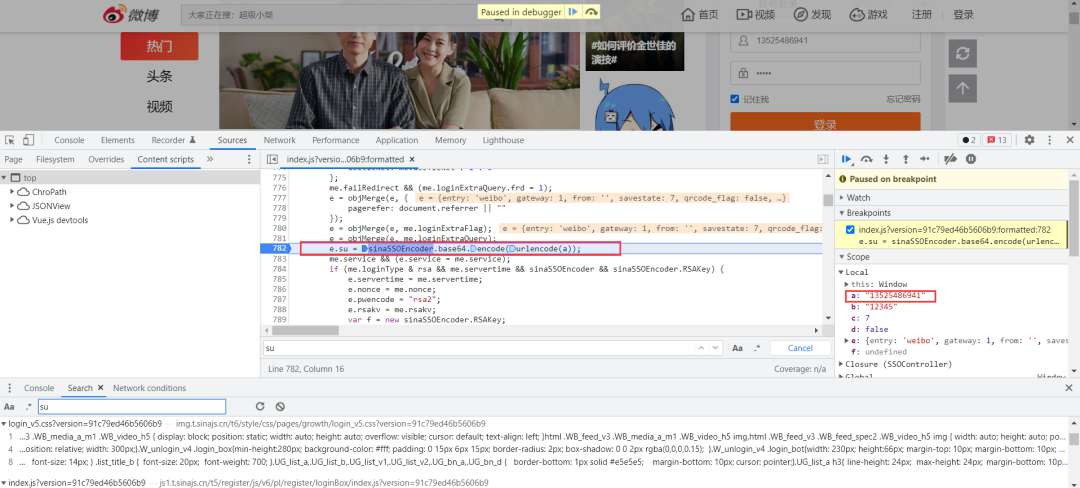
我们打断点分析,如下图所示,发现此处的**su**参数是输入的用户名经过base64算法加密,现在需要以相同方式模拟生成。知道这些内容后,通过复制网页中相关JS加密代码,在我们鬼鬼JS调试工具中运行生成加密内容。
3.加载JS代码
》》复制网页中JS代码
》》运行JS代码

#鬼鬼JS调试工具代码
function get_su(){
var sinaSSOEncoder = sinaSSOEncoder || {};
(function() {
var a = 0
, b = 8;
this.hex_sha1 = function(a) {
return i(c(h(a), a.length * b))
}
;
var c = function(a, b) {
a[b >> 5] |= 128 << 24 - b % 32;
a[(b + 64 >> 9 << 4) + 15] = b;
var c = Array(80)
, h = 1732584193
, i = -271733879
, j = -1732584194
, k = 271733878
, l = -1009589776;
for (var m = 0; m < a.length; m += 16) {
var n = h
, o = i
, p = j
, q = k
, r = l;
for (var s = 0; s < 80; s++) {
s < 16 ? c[s] = a[m + s] : c[s] = g(c[s - 3] ^ c[s - 8] ^ c[s - 14] ^ c[s - 16], 1);
var t = f(f(g(h, 5), d(s, i, j, k)), f(f(l, c[s]), e(s)));
l = k;
k = j;
j = g(i, 30);
i = h;
h = t
}
h = f(h, n);
i = f(i, o);
j = f(j, p);
k = f(k, q);
l = f(l, r)
}
return [h, i, j, k, l]
}
, d = function(a, b, c, d) {
return a < 20 ? b & c | ~b & d : a < 40 ? b ^ c ^ d : a < 60 ? b & c | b & d | c & d : b ^ c ^ d
}
, e = function(a) {
return a < 20 ? 1518500249 : a < 40 ? 1859775393 : a < 60 ? -1894007588 : -899497514
}
, f = function(a, b) {
var c = (a & 65535) + (b & 65535)
, d = (a >> 16) + (b >> 16) + (c >> 16);
return d << 16 | c & 65535
}
, g = function(a, b) {
return a << b | a >>> 32 - b
}
, h = function(a) {
var c = []
, d = (1 << b) - 1;
for (var e = 0; e < a.length * b; e += b)
c[e >> 5] |= (a.charCodeAt(e / b) & d) << 24 - e % 32;
return c
}
, i = function(b) {
var c = a ? "0123456789ABCDEF" : "0123456789abcdef"
, d = "";
for (var e = 0; e < b.length * 4; e++)
d += c.charAt(b[e >> 2] >> (3 - e % 4) * 8 + 4 & 15) + c.charAt(b[e >> 2] >> (3 - e % 4) * 8 & 15);
return d
}
, j = function(a) {
var b = ""
, c = 0;
for (; c < a.length; c++)
b += "%" + k(a[c]);
return decodeURIComponent(b)
}
, k = function(a) {
var b = "0" + a.toString(16);
return b.length <= 2 ? b : b.substr(1)
};
this.base64 = {
encode: function(a) {
a = "" + a;
if (a == "")
return "";
var b = "", c, d, e = "", f, g, h, i = "", j = 0;
do {
c = a.charCodeAt(j++);
d = a.charCodeAt(j++);
e = a.charCodeAt(j++);
f = c >> 2;
g = (c & 3) << 4 | d >> 4;
h = (d & 15) << 2 | e >> 6;
i = e & 63;
isNaN(d) ? h = i = 64 : isNaN(e) && (i = 64);
b = b + this._keys.charAt(f) + this._keys.charAt(g) + this._keys.charAt(h) + this._keys.charAt(i);
c = d = e = "";
f = g = h = i = ""
} while (j < a.length);
return b
},
decode: function(a, b, c) {
var d = function(a, b) {
for (var c = 0; c < a.length; c++)
if (a[c] === b)
return c;
return -1
};
typeof a == "string" && (a = a.split(""));
var e = [], f, g, h = "", i, j, k, l = "";
a.length % 4 == 0;
var m = /[^A-Za-z0-9+\\/=]/
, n = this._keys.split("");
if (b == "urlsafe") {
m = /[^A-Za-z0-9-_=]/;
n = this._keys_urlsafe.split("")
}
if (b == "subp_v2") {
m = /[^A-Za-z0-9_=-]/;
n = this._subp_v2_keys.split("")
}
if (b == "subp_v3_3") {
m = /[^A-Za-z0-9-_.-]/;
n = this._subp_v3_keys_3.split("")
}
var o = 0;
if (b == "binnary") {
n = [];
for (o = 0; o <= 64; o++)
n[o] = o + 128
}
if (b != "binnary" && m.test(a.join("")))
return c == "array" ? [] : "";
o = 0;
do {
i = d(n, a[o++]);
j = d(n, a[o++]);
k = d(n, a[o++]);
l = d(n, a[o++]);
f = i << 2 | j >> 4;
g = (j & 15) << 4 | k >> 2;
h = (k & 3) << 6 | l;
e.push(f);
k != 64 && k != -1 && e.push(g);
l != 64 && l != -1 && e.push(h);
f = g = h = "";
i = j = k = l = ""
} while (o < a.length);
if (c == "array")
return e;
var p = ""
, q = 0;
for (; q < e.lenth; q++)
p += String.fromCharCode(e[q]);
return p
},
_keys: "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=",
_keys_urlsafe: "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789-_=",
_subp_v2_keys: "uAL715W8e3jJCcNU0lT_FSXVgxpbEDdQ4vKaIOH2GBPtfzqsmYZo-wRM9i6hynrk=",
_subp_v3_keys_3: "5WFh28sGziZTeS1lBxCK-HgPq9IdMUwknybo.LJrQD3uj_Va7pE0XfcNR4AOYvm6t"
};
this.Cookie = {
decode: function(a) {
var b = []
, c = a.substr(0, 3)
, d = a.substr(3);
switch (c) {
case "v01":
for (var e = 0; e < d.length; e += 2)
b.push(parseInt(d.substr(e, 2), 16));
return decodeURIComponent(j(sinaSSOEncoder.base64.decode(b, "binnary", "array")));
case "v02":
d = d.replace(/\\./g, "=");
b = sinaSSOEncoder.base64.decode(d, "urlsafe", "array");
return j(sinaSSOEncoder.base64.decode(b, "binnary", "array"));
default:
return decodeURIComponent(a)
}
}
};
this.getSUBPCookie = {
__parse: function(a) {
var b, c, d, e, f, g = 0, h, i = {}, k = "", l = "";
if (!a)
return i;
do {
c = a[g];
b = ++g;
for (h = g; h < c + b; h++,
g++)
k += String.fromCharCode(a[h]);
e = a[g];
b = ++g;
if (k == "status" || k == "flag")
for (h = g; h < e + b; h++,
g++)
l += a[h];
else {
l = a.slice(b, e + b);
try {
l = j(l)
} catch (m) {
l = ""
}
g += e
}
i[k] = l;
k = "";
l = ""
} while (g < a.length);
return i
},
decode: function(a) {
var b = [], c, d = a.substr(0, 3), e = decodeURIComponent(a.substr(3));
switch (d) {
case "002":
b = sinaSSOEncoder.base64.decode(e, "subp_v2", "array");
return sinaSSOEncoder.getSUBPCookie.__parse(b);
case "003":
c = e.substr(0, 1);
e = e.substr(1);
b = sinaSSOEncoder.base64.decode(e, "subp_v3_" + c, "array");
return sinaSSOEncoder.getSUBPCookie.__parse(b);
default:
return decodeURIComponent(a)
}
}
}
}
).call(sinaSSOEncoder);
urlencode = function(a) {
return encodeURIComponent(a)
}
su = sinaSSOEncoder.base64.encode(urlencode("13525486941"))
return su
}
与我们发的POST请求参数相同,说明我们成功地破解该参数。

4.Python运行JS文件
》》导入包名
》》加载文件
》》编译文件
》》调用函数
import execjs
#生成su
def get_su():
#读入JS脚本文件
with open('weibo_su.js', 'r', encoding='utf-8') as f:
content = f.read()
#编译JS代码
jsdata = execjs.compile(content)
#调用函数
wb_su = jsdata.call('get_su')
#输出结果
print('wb_su:', wb_su)
#运行函数,输出也是相同的
get_su()

声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
浅谈加密芯片的一种破解方法和加密方案改进设计2024-12-20 1253
-
python爬虫之某站JS加密逆向分析2023-05-05 2530
-
Python怎么玩转JS脚本2023-02-23 1958
-
STM32 ID加密,防破解读id最关键的注意点2022-08-20 8856
-
labview的VI加密暴力破解工具2021-09-03 3300
-
批量破解VI密码、加密和移除VI面板的应用程序2021-07-08 2003
-
彩虹加密狗破解技巧数据代码分析2019-01-24 1270
-
大神加密WiFi怎么破解密码2019-01-09 5125
-
exew文件加密:利用破解版exe文件加密器对exe文件进行加密保护2018-12-19 2198
-
请问有谁需要破解加密VI??2018-06-08 2385
-
VI被加密环境加密,如何破解2016-08-10 5902
-
2704R加密芯片已破解,有替代方案2015-05-16 6420
-
加密数字信号破解2013-10-28 2083
-
破解labview后台加密程序2012-09-25 14296
全部0条评论

快来发表一下你的评论吧 !

