

初识内存取证-volatility与Easy_dump
电子说
1.4w人已加入
描述
volatility
Volatility是一款非常强大的内存取证工具,它是由来自全世界的数百位知名安全专家合作开发的一套工具, 可以用于windows,linux,mac osx,android等系统内存取证。Volatility是一款开源内存取证框架,能够对导出的内存镜像进行分析,通过获取内核数据结构,使用插件获取内存的详细情况以及系统的运行状态。 在不同系统下都有不同的软件版本,官网地址:https://www.volatilityfoundation.org/26volatility工具的基本使用
命令格式
volatility -f [image] --profile=[profile] [plugin]
在分析之前,需要先判断当前的镜像信息,分析出是哪个操作系统volatility -f xxx.vmem imageinfo如果操作系统错误,是无法正确读取内存信息的,知道镜像后,就可以在--profile=中带上对应的操作系统
常用插件
下列命令以windows内存文件举例查看用户名密码信息
volatility -f 1.vmem --profile=Win7SP1x64 hashdump查看进程
volatility -f 1.vmem --profile=Win7SP1x64 pslist查看服务
volatility -f 1.vmem --profile=Win7SP1x64 svcscan查看浏览器历史记录
volatility -f 1.vmem --profile=Win7SP1x64 iehistory查看网络连接
volatility -f 1.vmem --profile=Win7SP1x64 netscan查看命令行操作
volatility -f 1.vmem --profile=Win7SP1x64 cmdscan查看文件
volatility -f 1.vmem --profile=Win7SP1x64 filescan查看文件内容
volatility -f 1.vmem --profile=Win7SP1x64 dumpfiles -Q 0xxxxxxxx -D ./查看当前展示的notepad内容
volatility -f 1.vmem --profile=Win7SP1x64 notepad提取进程
volatility -f 1.vmem --profile=Win7SP1x64 memdump -p xxx --dump-dir=./屏幕截图
volatility -f 1.vmem --profile=Win7SP1x64 screenshot --dump-dir=./查看注册表配置单元
volatility -f 1.vmem --profile=Win7SP1x64 hivelist查看注册表键名
volatility -f 1.vmem --profile=Win7SP1x64 hivedump -o 0xfffff8a001032410查看注册表键值
volatility -f 1.vmem --profile=Win7SP1x64 printkey -K "xxxxxxx"查看运行程序相关的记录,比如最后一次更新时间,运行过的次数等
volatility -f 1.vmem --profile=Win7SP1x64 userassist最大程序提取信息
volatility -f 1.vmem --profile=Win7SP1x64 timeliner
电子取证之Easy_dump(2018护网杯)
查看镜像信息
volatility -f easy_dump.img imageinfo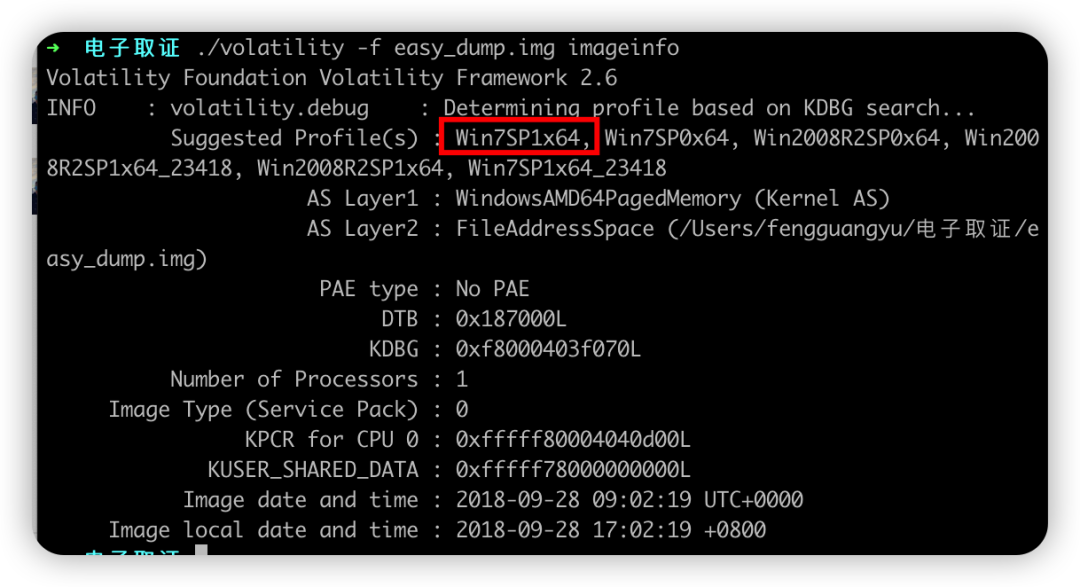
查看结果,推测可能是Win7SP1x64的镜像
指定镜像进行进程扫描
volatility -f easy_dump.img --profile=Win7SP1x64 psscan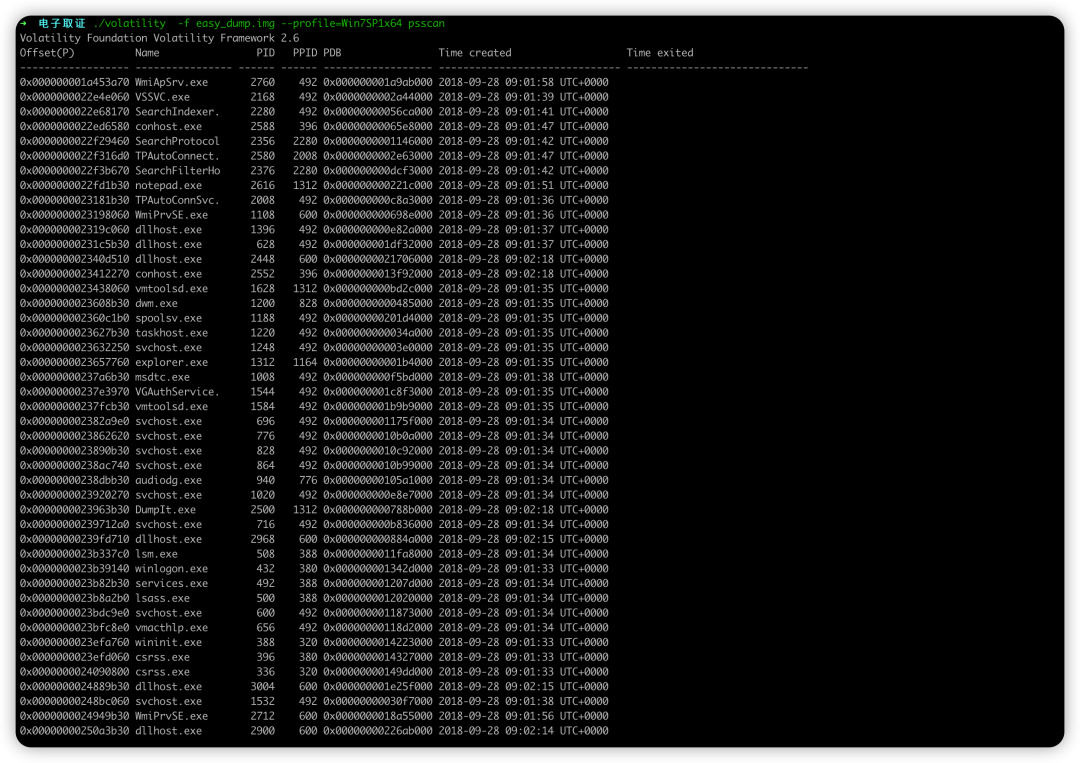
也可以使用pslist参数
发现存在notepad.exe,查看一下内容。
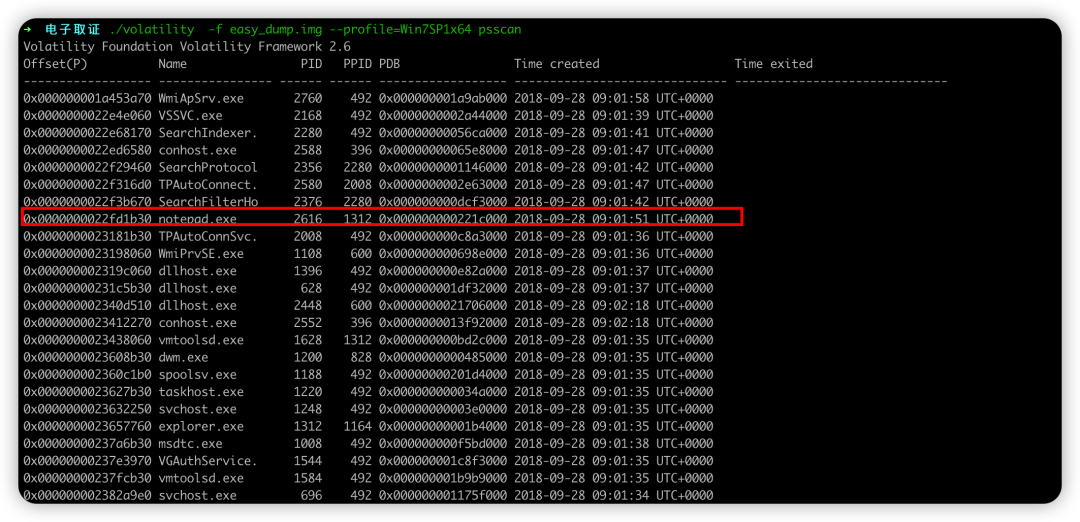
导出进程中内容
volatility -f easy_dump.img --profile=Win7SP1x64 memdump -p 2616 -D /xxx/xxx/xxx/其中procdump:是提取进程的可执行文件
memdump:是提取进程在内存中的信息
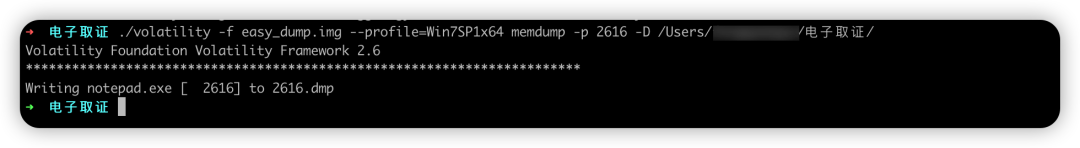
使用strings查找flag信息
strings -e l 2616.dmp | grep "flag"发现提示是jpg
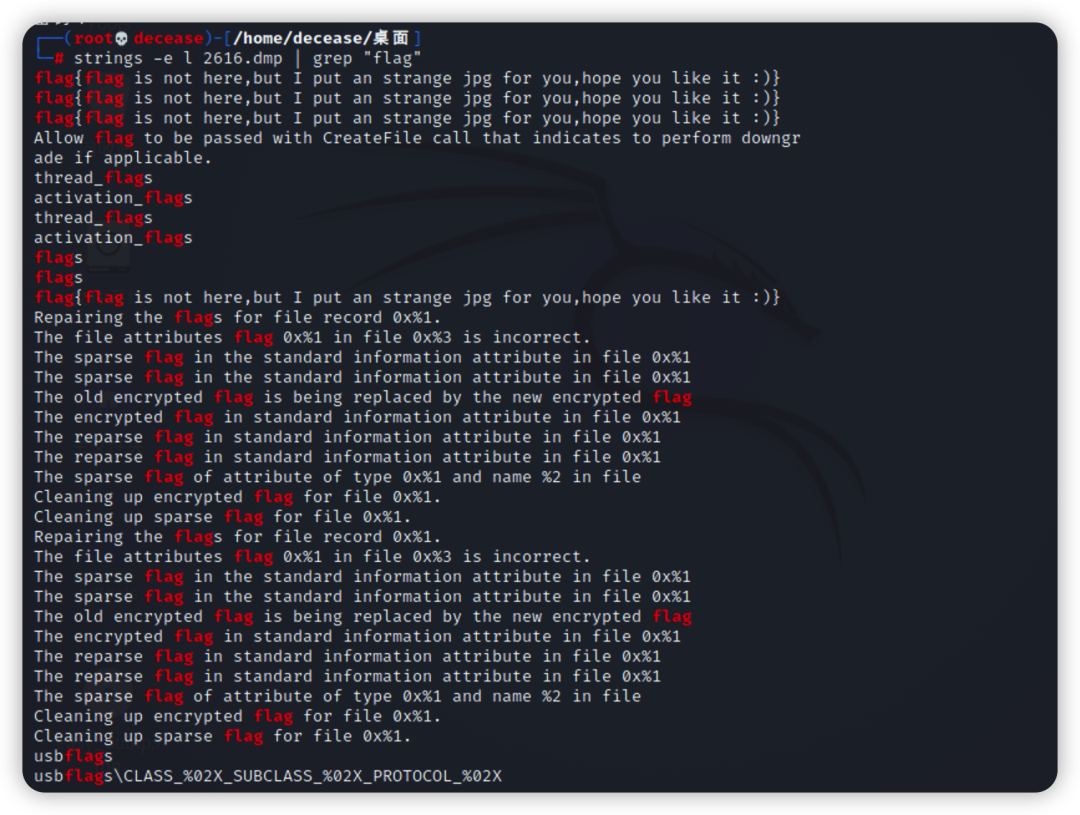
读取jpg文件
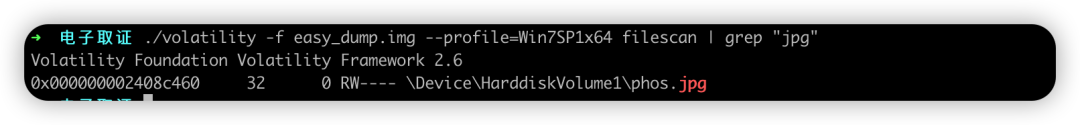
volatility -f easy_dump.img --profile=Win7SP1x64 filescan | grep "jpg"发现图片phos.jpg
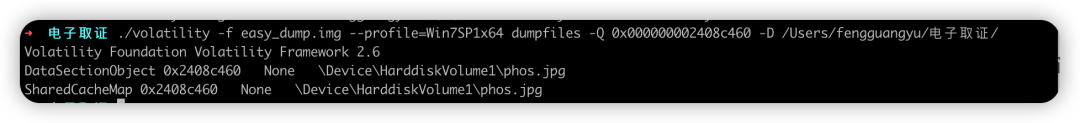
导出图片
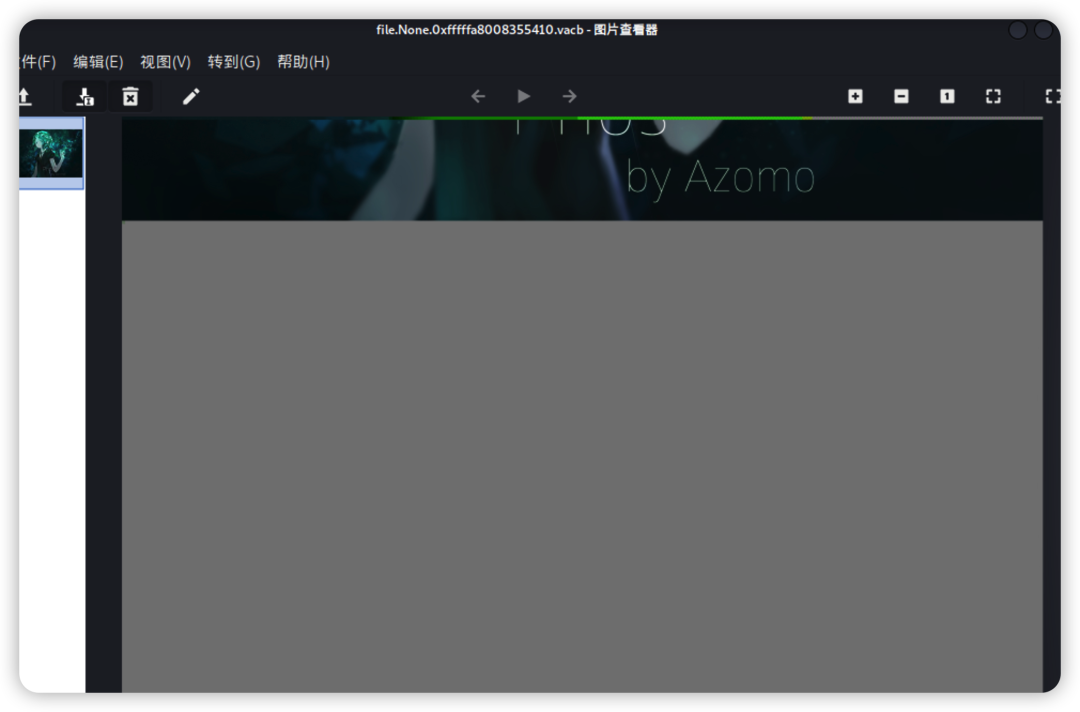
查看图片,无法正常打开
使用binwalk查看,发现存在zip文件
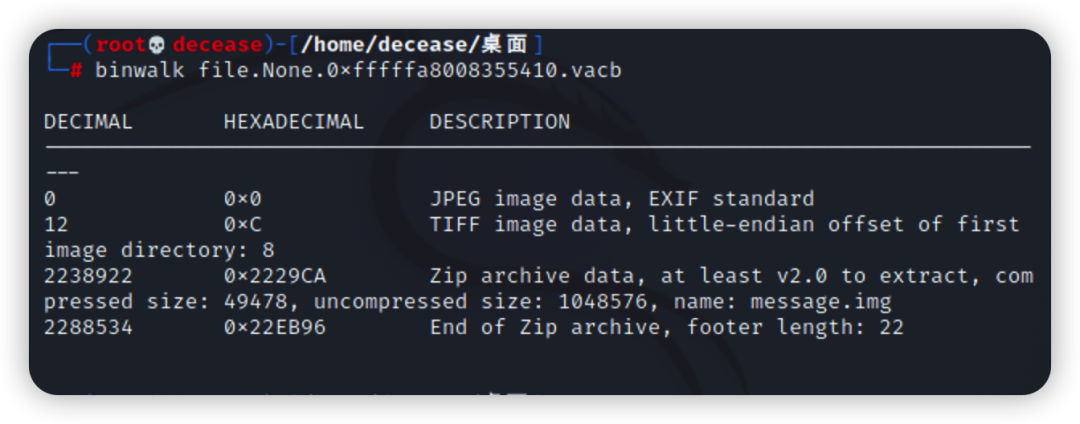
分离文件
foremost file.None.0xfffffa8008355410.vacb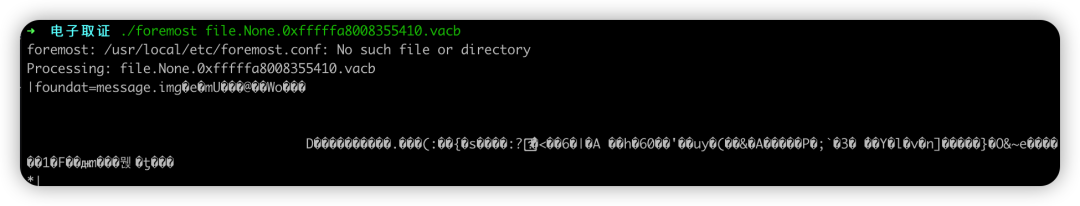
分离后自动生成output文件夹,查看内容
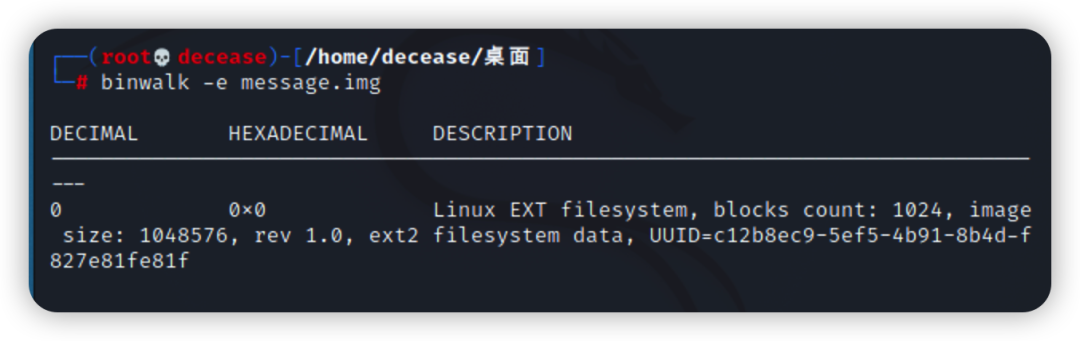
解压00004372.zip,得到message.img
继续使用binwalk提取文件
得到hint.txt
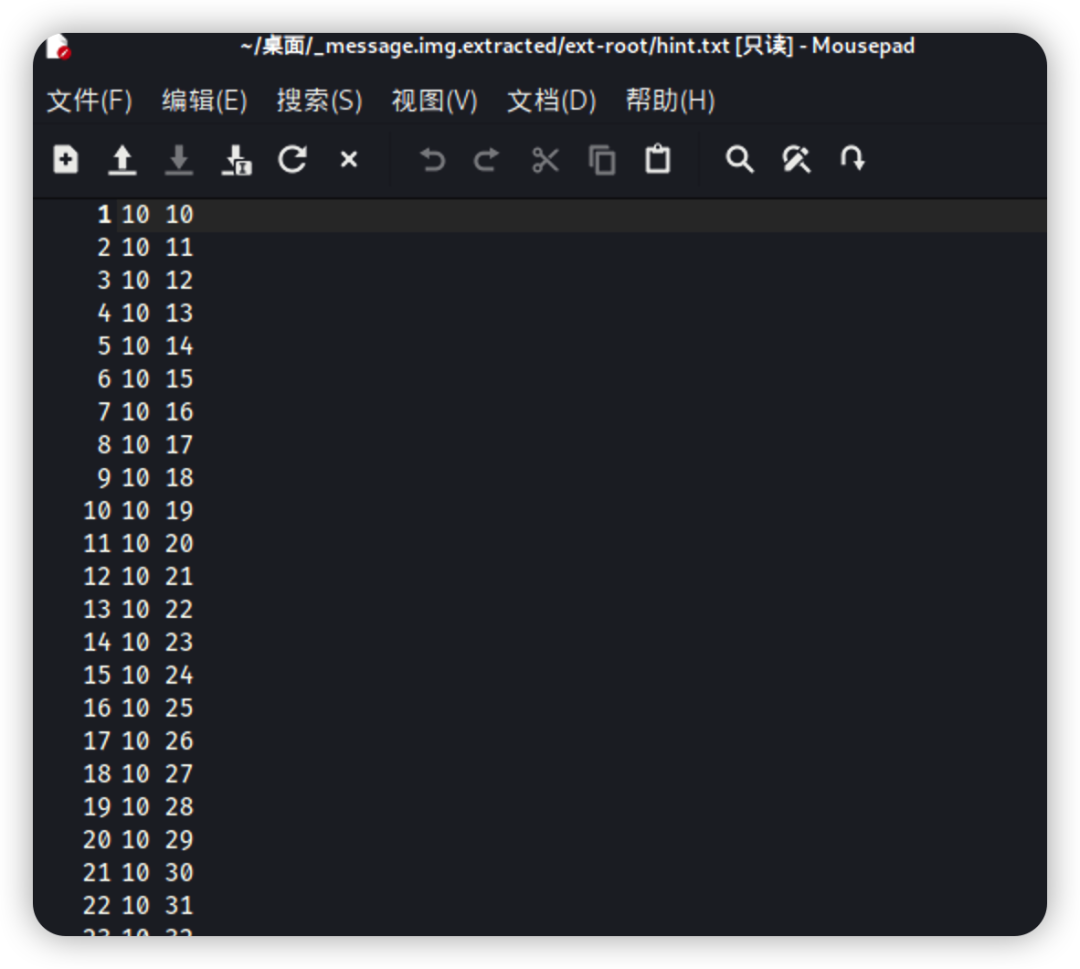
使用脚本进行转换
查看其他大佬说可能是左边,使用脚本进行转换#脚本文件 import matplotlib.pyplot as plt import numpy as np x = [] y = [] with open('hint.txt','r') as f: datas = f.readlines() for data in datas: arr = data.split(' ') x.append(int(arr[0])) y.append(int(arr[1])) plt.plot(x,y,'ks',ms=1) plt.show()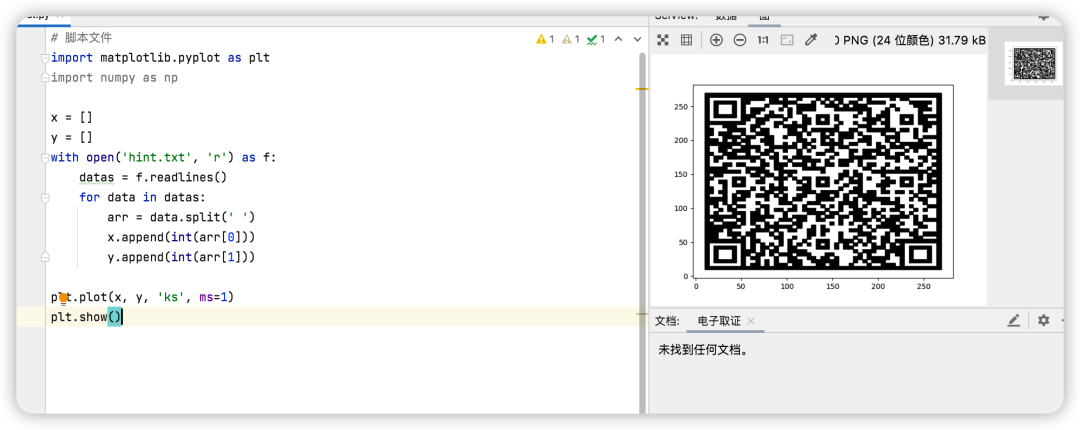 扫描二维码得到提示,一个是维吉尼亚加密,秘钥是aeolus。一个是加密文件被删除了,需要恢复。
扫描二维码得到提示,一个是维吉尼亚加密,秘钥是aeolus。一个是加密文件被删除了,需要恢复。
恢复文件
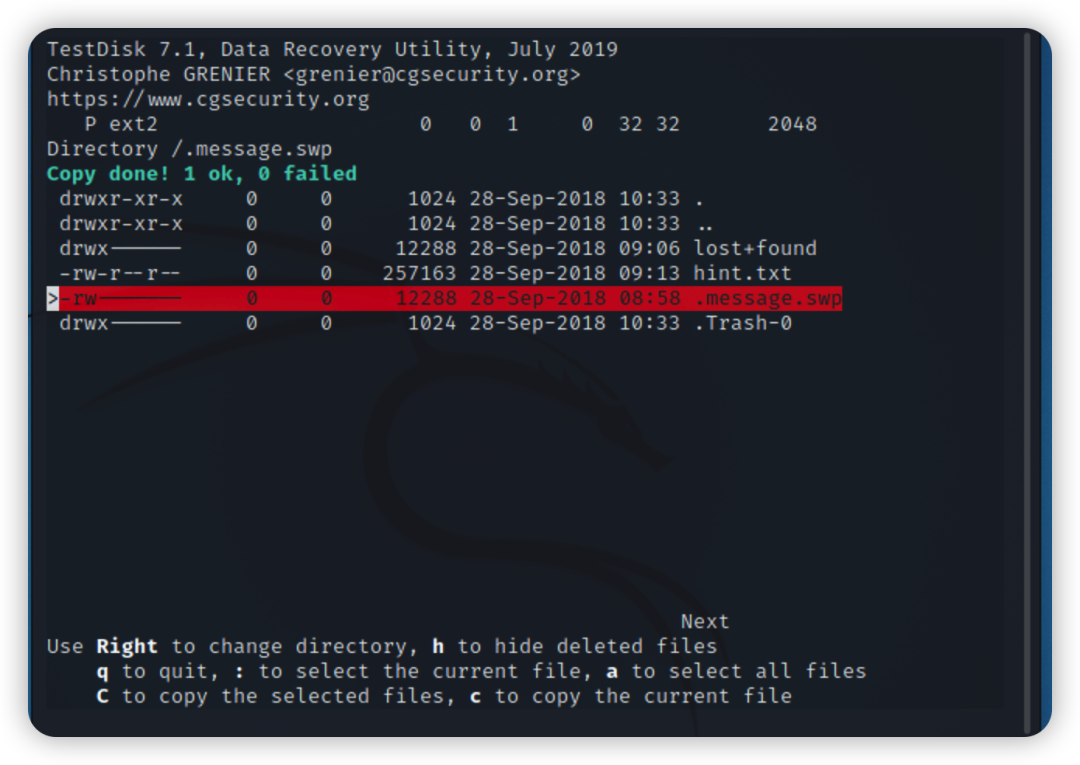
使用testdisk进行恢复 testdisk message.img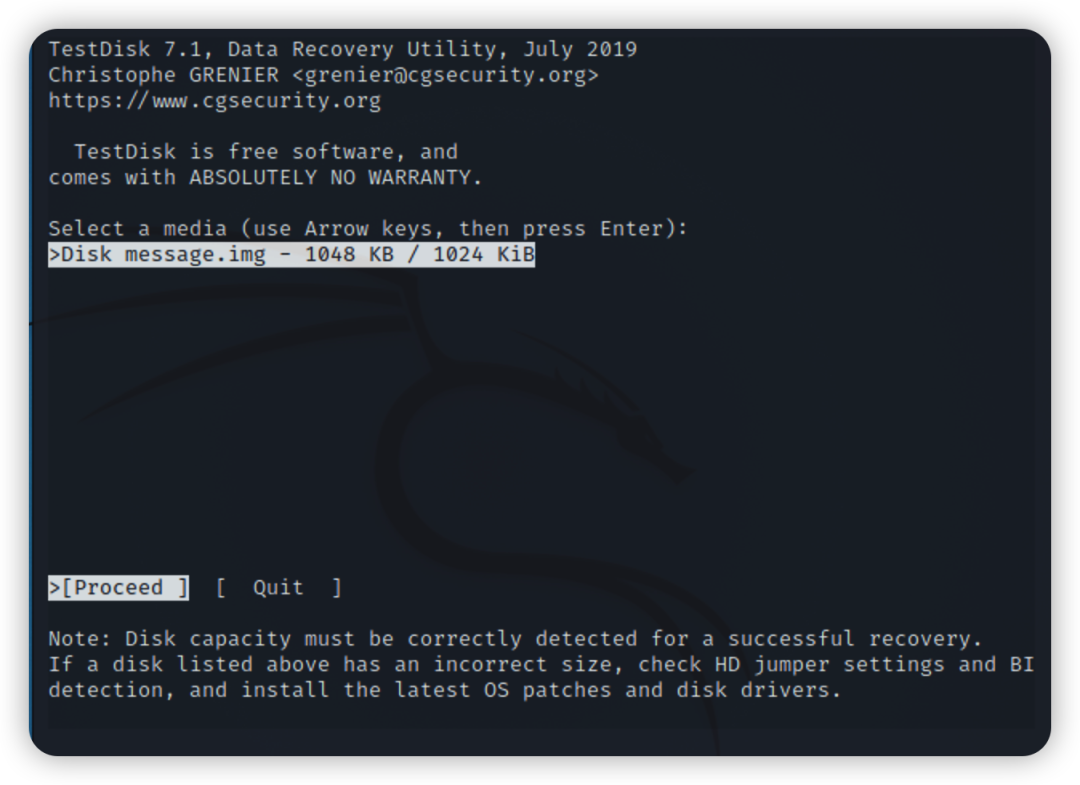 红色为需要恢复的文件
红色为需要恢复的文件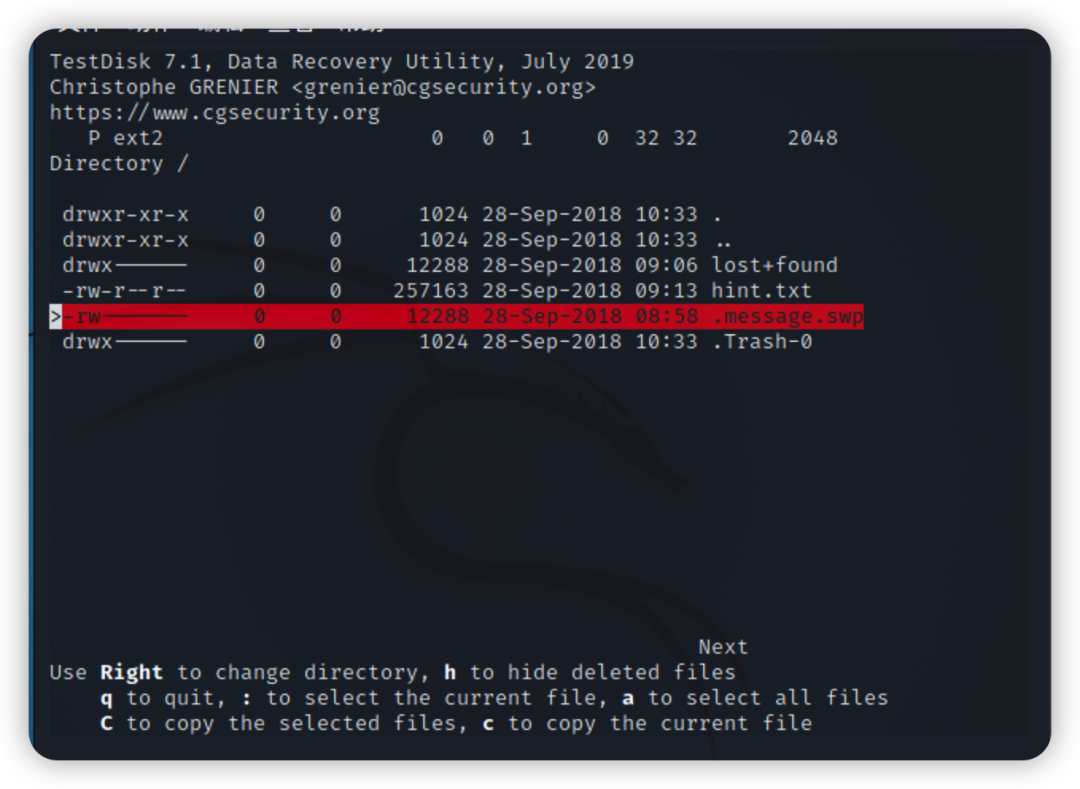
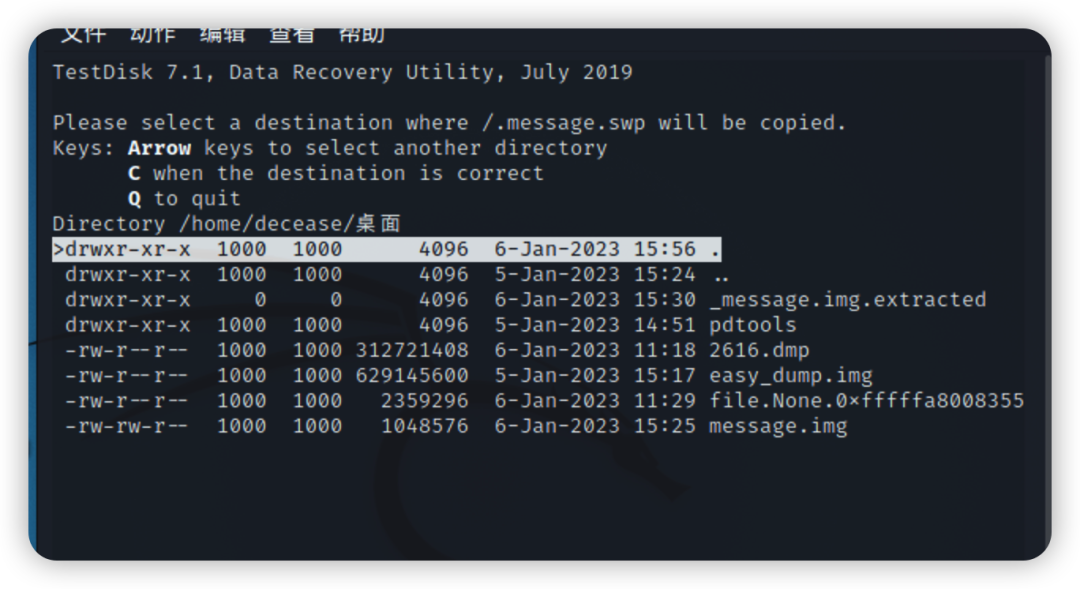
 使用ls -a查看
使用ls -a查看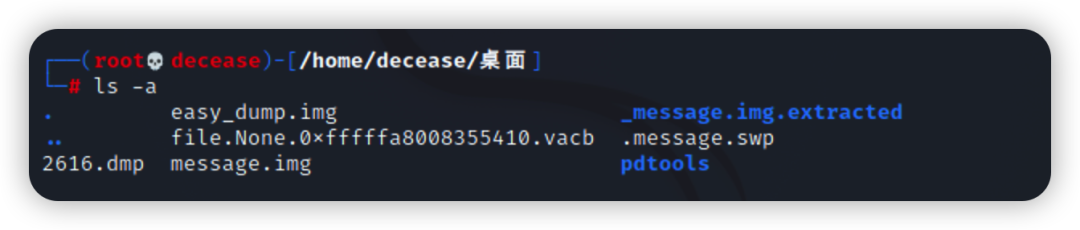 使用strings查看
使用strings查看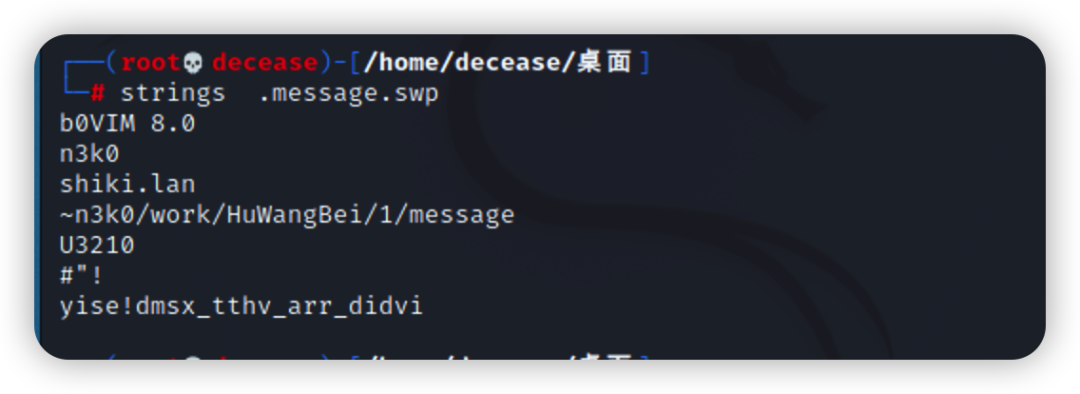 最后一句字符串尝试解密 得到最终结果
最后一句字符串尝试解密 得到最终结果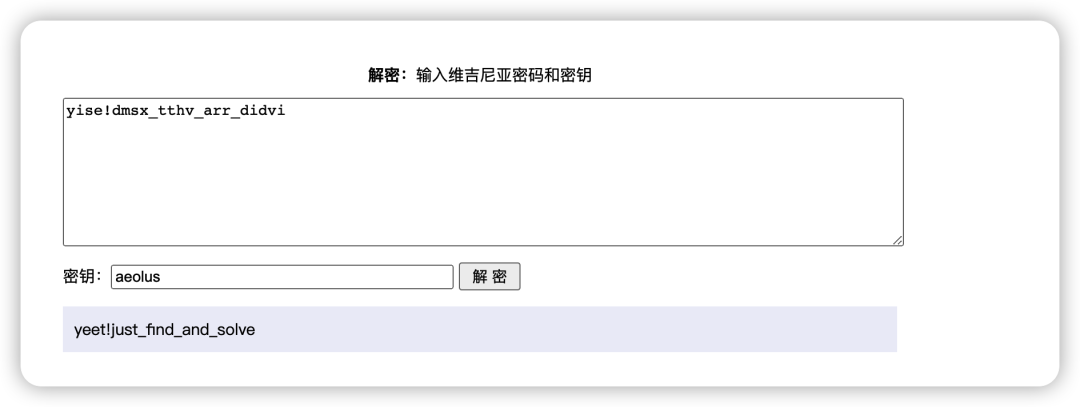
参考资料
https://www.cnblogs.com/zaqzzz/p/10350989.html https://blog.csdn.net/weixin_42742658/article/details/106819187
审核编辑 :李倩
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
jmap dump内存的命令是2023-12-05 4113
-
Windows内存取证知识浅析-上篇2023-11-29 1898
-
虹科分享 | 关于内存取证你应该知道的那些事2023-08-01 2173
-
Volatility取证大杀器2022-10-28 5123
-
内存取证之Volatility从0到1编程设计2022-09-26 1348
-
内存是怎么存取数据的2022-09-16 4948
-
SCL-CPU内存区域的索引存取2022-06-02 2004
-
简述SCL -CPU内存区域的索引存取2021-04-16 2844
-
基于浮点系列芯片ADSP2106x中的直接内存存取技术研究2020-07-10 1525
-
为什么我使用dump_image将内存内容dump出来后和原始文件相差很大?2019-07-11 3292
-
你知道Linux Core Dump是什么?2019-05-10 3239
-
内存取证的内核完整性度量方法2018-01-10 955
-
基于内存云的大块数据对象并行存取策略2017-12-17 720
-
DMA—直接内存存取2017-12-13 983
全部0条评论

快来发表一下你的评论吧 !

