

如何利用NAT技术隐藏GRE报文中的源地址信息?
制造/封装
536人已加入
描述
组网及说明
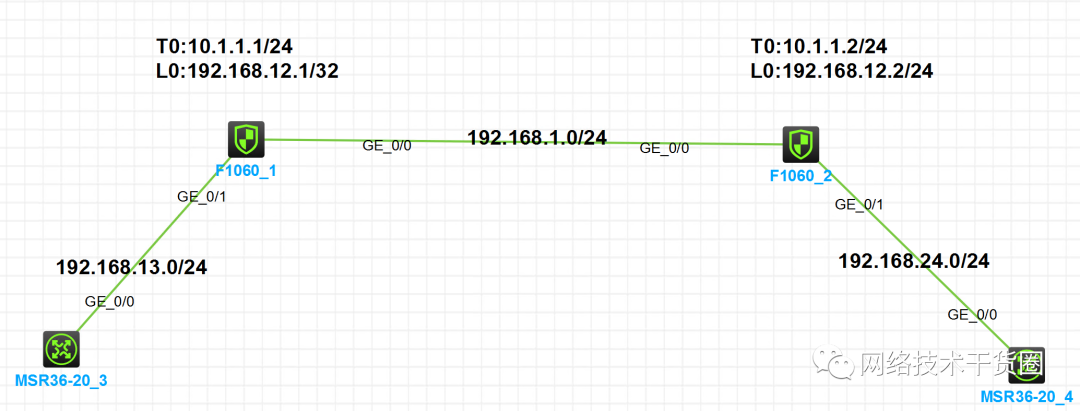
注:如无特别说明,描述中的 FW1 或 MSR1 对应拓扑中设备名称末尾数字为 1 的设备,FW2 或 MSR2 对应拓扑中设备名称末尾数字为 2 的设备,以此类推;另外,同一网段中,IP 地址的主机位为其设备编号,如 FW1 的 g0/0 接口若在 192.168.1.0/24 网段,则其 IP 地址为 192.168.1.1/24,以此类推。
实验需求
由于GRE报文为明文封装,在网络中传输容易被监听导致信息泄漏。基于此,本案例提供一种方案,使用NAT技术隐藏客户端源地址。
配置步骤
FW1
# nat static inbound 192.168.13.3 1.1.1.1 acl 3000 reversible # interface LoopBack0 ip address 192.168.12.1 255.255.255.255 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 192.168.1.1 255.255.255.0 nat outbound # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 192.168.13.1 255.255.255.0 nat static enable # interface Tunnel0 mode gre ip address 10.1.1.1 255.255.255.0 source 192.168.12.1 destination 192.168.12.2 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/1 # security-zone name DMZ # security-zone name Untrust import interface GigabitEthernet1/0/0 import interface Tunnel0 # security-zone name Management # ip route-static 1.1.1.1 32 192.168.13.3 ip route-static 1.1.1.2 32 Tunnel0 ip route-static 192.168.12.2 32 192.168.1.2 ip route-static 192.168.24.4 32 Tunnel0 # acl advanced 3000 rule 5 permit ip source 192.168.13.3 0 destination 1.1.1.2 0 # session statistics enable # ip http enable ip https enable # security-policy ip rule 0 name any action pass
FW2
# nat static inbound 192.168.24.4 1.1.1.2 acl 3000 reversible # interface LoopBack0 ip address 192.168.12.2 255.255.255.255 # interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 192.168.1.2 255.255.255.0 nat outbound # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 192.168.24.2 255.255.255.0 nat static enable # interface Tunnel0 mode gre ip address 10.1.1.2 255.255.255.0 source 192.168.12.2 destination 192.168.12.1 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/1 # security-zone name DMZ # security-zone name Untrust import interface GigabitEthernet1/0/0 import interface Tunnel0 # security-zone name Management # ip route-static 1.1.1.1 32 Tunnel0 ip route-static 1.1.1.2 32 192.168.24.4 ip route-static 192.168.12.1 32 192.168.1.1 ip route-static 192.168.13.3 32 Tunnel0 # acl advanced 3000 rule 5 permit ip source 192.168.24.4 0 destination 1.1.1.1 0 # session statistics enable # ip http enable ip https enable # security-policy ip rule 0 name any action pass
配置关键点
注意事项:需要注意添加对应的静态路由
以R3访问R4为例,访问过程如下:
FW1上的业务点
NAT转换:
192.168.13.3:10965 - 1.1.1.2: 2048(VPN: 0) ------> 1.1.1.1:10965 - 1.1.1.2: 2048(VPN: 0)
GRE封装:
192.168.12.1 - 192.168.12.2
W2上的业务点
GRE解封装:
192.168.12.1 - 192.168.12.2
NAT转换:
1.1.1.1:10965 - 1.1.1.2: 2048(VPN: 0) ------> 1.1.1.1:10965 - 192.168.24.4: 2048(VPN: 0)
审核编辑:刘清
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
怎样设置tc的dma寄存器,使其源地址不变目的地址偏移?2024-02-19 490
-
STM32F429能否通过设置源地址滤过将非业务主机的arp广播报文滤掉?2023-08-07 391
-
请问DMA源地址如果是全局变量那源地址那里应该怎么填呢?2023-06-13 1359
-
MIMXRT1170-EVK是否可以使用递减源地址设置EDMA?2023-03-21 462
-
穿越NAT的SDWAN技术实现(上)2022-10-11 2260
-
C6657的EDMA源地址设置为CONST模式时接收到的数据全部为02019-01-11 3744
-
请问DM8148和DM8168 EDMA3 源地址和目标地址有没有字节对齐要求?2018-07-27 1562
-
EDMA3中源地址和目的地址设置问题2018-06-21 1849
-
互联网自治域间IP源地址验证技术综述2017-12-19 778
-
华泰电动汽车节点源地址2017-10-26 4467
-
网络地址转换课件2011-04-14 967
全部0条评论

快来发表一下你的评论吧 !

