

基于V682-SONiC交换机的实现网络丢包检测的可视化
通信网络
描述
引言
随着超大型数据中心的出现和RDMA(远程直接内存访问技术)技术的普及,对网络运维提出的要求越来越高,只靠传统的网络监控技术如SNMP/CLI/log已经无法满足。Telemetry是一项监控设备性能和故障的远程数据采集技术,获取的监控数据拥有更高的精度和更加实时。特别是基于订阅服务的Stream模式可以由网络设备本身进行信息上报,从而有效减轻数据采集器维持监控的负载。
SONiC作为专注于数据中心的开源网络系统,架构设计就是将各个模块放置在独立的docker中,基于redis-database在各个子系统之间进行数据持久化、复制和多进程通信。基于gRPC的Telemetry技术可以采集Redis-database中存储的设备接口流量等信息后,经过Protocol Buffer编码,实时上报给采集器进行接收和存储,供分析器读取。
网络丢包是网络通信中较为常见的故障,越早获取到丢包信息和丢包原因才可能越早进行排障。SONiC的drop counter功能可以将交换芯片对丢包信息的监控能力呈现给Telemetry模块,不但可以快速检测到丢包的出现,还能检测出丢包的原因,从而很好地解决数据中心网络中这一痛点问题。下面的演示以telemetry采集盛科V682-SONiC交换机的drop counter为例,通过一系列开源软件实现网络丢包检测的可视化。
环境搭建
综述
验证环境的拓扑图如下
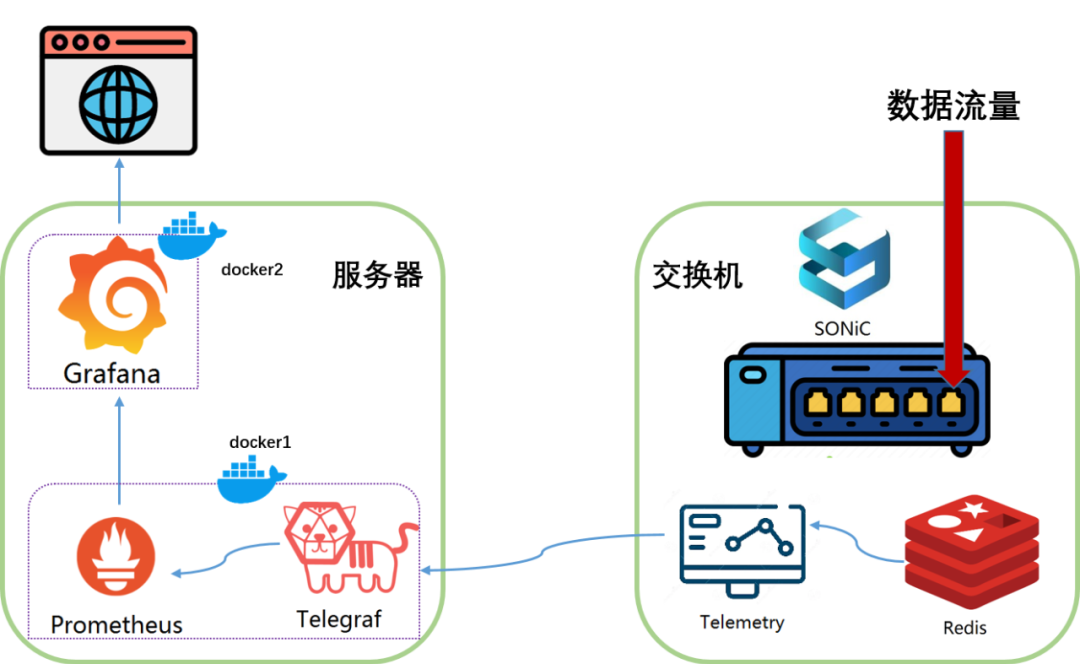
服务器运行两个docker
docker1运行Telegraf和Prometheus
Prometheus是一款基于时序数据库的开源系统监控和报警系统。
Telegraf是一款基于插件驱动开源数据收集Agent。此处是用支持sonic-telemetry的分支版本编译,实现将sonic-telemetry数据转化为Prometheus能够识别的数据格式
docker2运行Grafana
Grafana 是一款开源数据可视化工具,可以做数据监控和数据统计,带有告警功能
因此监控数据的走向就是Telemetry->Telegraf->Prometheus->Grafana,最后在Grafana对外提供的Web上进行可视化展示
交换机上的操作
SONiC交换机添加VLAN10和VLAN60,Ethernet7加入到VLAN60,在VLAN60上配置60.1.1.254/24
admin@sonic:~$ sudo config vlan add 10 admin@sonic:~$ sudo config vlan add 60 admin@sonic:~$ sudo config vlan member add 60 Ethernet7 admin@sonic:~$ sudo config interface ip add Vlan60 60.1.1.254/24
SONiC交换机进入telemetry docker,启动Telemetry服务,监听8181端口
admin@sonic:~$ docker exec -it telemetry bash root@sonic:/# /usr/sbin/telemetry -logtostderr --insecure --port 8181 --allow_no_client_auth -v=2
SONiC交换机上添加INGRESS_VLAN_FILTER和LPM4_MISS两个丢包原因
admin@sonic:~$ sudo config dropcounters install DEBUG_VLAN_TAG_MISMATCH PORT_INGRESS_DROPS [INGRESS_VLAN_FILTER] admin@sonic:~$ admin@sonic:~$ sudo config dropcounters install DEBUG_ROUTE_MISMATCH PORT_INGRESS_DROPS [LPM4_MISS] admin@sonic:~$ admin@sonic:~$ show dropcounters configuration Counter Alias Group Type Reasons Description ----------------------- ----------------------- ------- ------------------ ------------------- ------------- DEBUG_ROUTE_MISMATCH DEBUG_ROUTE_MISMATCH N/A PORT_INGRESS_DROPS LPM4_MISS N/A DEBUG_VLAN_TAG_MISMATCH DEBUG_VLAN_TAG_MISMATCH N/A PORT_INGRESS_DROPS INGRESS_VLAN_FILTER N/A admin@sonic:~$
查看COUNTERS_DB,PORT下新增了两个field
admin@sonic:~$ sonic-db-cli COUNTERS_DB HGET COUNTERS:oid:0x10000000000c5 SAI_PORT_STAT_IN_CONFIGURED_DROP_REASONS_1_DROPPED_PKTS 0 admin@sonic:~$ sonic-db-cli COUNTERS_DB HGET COUNTERS:oid:0x10000000000c5 SAI_PORT_STAT_IN_CONFIGURED_DROP_REASONS_2_DROPPED_PKTS 0 admin@sonic:~$
docker1上的操作
服务器上准备好prometheus的配置文件/opt/prometheus/prometheus.yml
admin@admin-server:~$ cat /opt/prometheus/prometheus.yml global: scrape_interval: 2s evaluation_interval: 2s scrape_configs: - job_name: telegraf static_configs: - targets: ['127.0.0.1:9100'] labels: instance: localhost admin@admin-server:~$
以镜像ubuntu/prometheus:2.32-20.04_beta为基础运行docker1,将docker的9090端口映射到服务器的9191端口
admin@admin-server:~/telemetry$ docker run -d > -p 9191:9090 > -v /opt/prometheus/prometheus.yml:/etc/prometheus/prometheus.yml > --name prometheus > ubuntu/prometheus:2.32-20.04_beta
将编译好的telegram(包含sonic input plugin)可执行文件拷贝到docker1,并按照指定配置运行
root@31e2f2a810ca:/prometheus# cd /root/ root@31e2f2a810ca:~# ls -l total 92908 -rwxr-xr-x 1 1000 1000 95132120 Aug 12 17:31 telegraf -rw-r--r-- 1 1000 1000 578 Aug 27 06:33 telegraf.conf root@31e2f2a810ca:~# ls -t telegraf.conf telegraf root@31e2f2a810ca:~# ls telegraf telegraf.conf root@31e2f2a810ca:~# root@31e2f2a810ca:~# cat telegraf.conf [agent] debug = true [[inputs.sonic_telemetry_gnmi]] addresses = ["10.13.33.135:8181"] username = "admin" password = "YourPaSsWoRd" encoding = "json_ietf" redial = "10s" enable_tls = true insecure_skip_verify = true target = "COUNTERS_DB" [[inputs.sonic_telemetry_gnmi.subscription]] name = "test_135_ifcounters" origin = "" path = "/COUNTERS/Ethernet7" subscription_mode = "sample" sample_interval = "5s" [[outputs.prometheus_client]] listen = ":9100" metric_version = 2 root@31e2f2a810ca:~# root@31e2f2a810ca:~# ./telegraf --config telegraf.conf 2023-09-24T06:06:34Z I! Starting Telegraf 2023-09-24T06:06:34Z I! Loaded inputs: sonic_telemetry_gnmi 2023-09-24T06:06:34Z I! Loaded aggregators: 2023-09-24T06:06:34Z I! Loaded processors: 2023-09-24T06:06:34Z I! Loaded outputs: prometheus_client 2023-09-24T06:06:34Z I! Tags enabled: host=31e2f2a810ca 2023-09-24T06:06:34Z I! [agent] Config: Interval:10s, Quiet:false, Hostname:"31e2f2a810ca", Flush Interval:10s 2023-09-24T06:06:34Z D! [agent] Initializing plugins 2023-09-24T06:06:34Z D! [agent] Connecting outputs 2023-09-24T06:06:34Z D! [agent] Attempting connection to [outputs.prometheus_client] 2023-09-24T06:06:34Z I! [outputs.prometheus_client] Listening on http://[::]:9100/metrics 2023-09-24T06:06:34Z D! [agent] Successfully connected to outputs.prometheus_client 2023-09-24T06:06:34Z D! [agent] Starting service inputs 2023-09-24T06:06:35Z D! [inputs.sonic_telemetry_gnmi] Connection to GNMI device 10.13.33.135:8181 established 2023-09-24T06:06:44Z D! [outputs.prometheus_client] Wrote batch of 2 metrics in 665.355µs 2023-09-24T06:06:44Z D! [outputs.prometheus_client] Buffer fullness: 0 / 10000 metrics 2023-09-24T06:06:54Z D! [outputs.prometheus_client] Wrote batch of 1 metrics in 280.59µs 2023-09-24T06:06:54Z D! [outputs.prometheus_client] Buffer fullness: 0 / 10000 metrics 2023-09-24T06:07:04Z D! [outputs.prometheus_client] Wrote batch of 1 metrics in 305.204µs 2023-09-24T06:07:04Z D! [outputs.prometheus_client] Buffer fullness: 0 / 10000 metrics ......
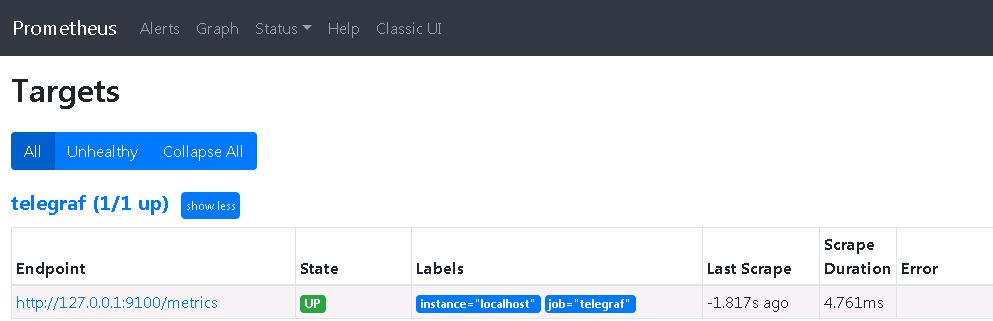
打开Prometheus的targets页面,确认telegaf源已经up
docker2上的操作
以镜像philhawthorne/docker-influxdb-grafana:latest为基础运行docker2
admin@admin-server:~$ docker run -d > --name docker-influxdb-grafana > -p 3003:3003 > -p 3004:8083 > -p 8086:8086 > -v /home/admin/influxdb:/var/lib/influxdb > -v /home/admin/grafana:/var/lib/grafana > philhawthorne/docker-influxdb-grafana:latest
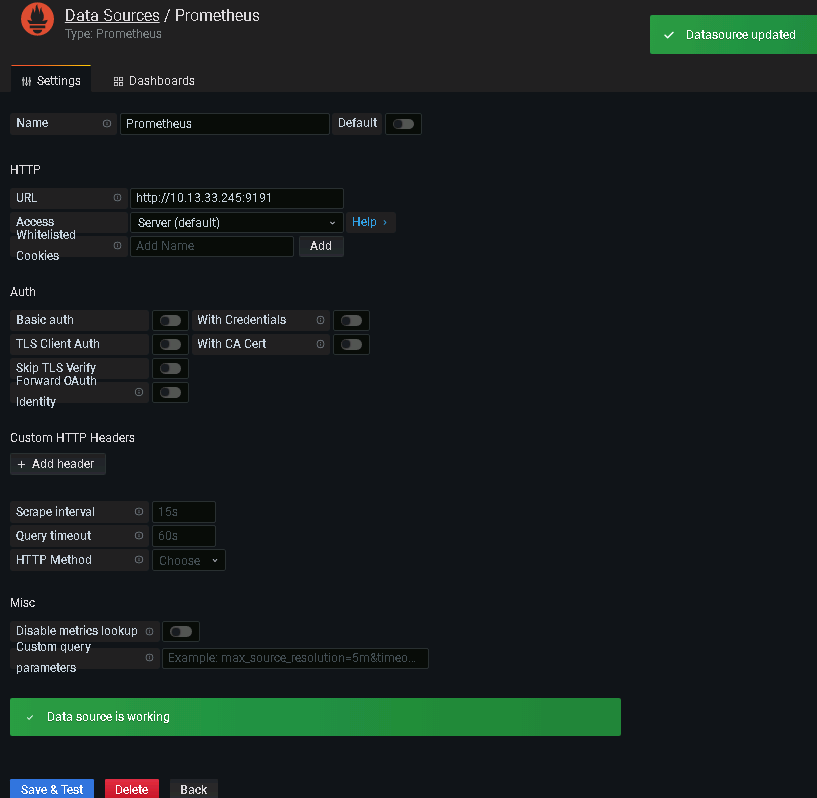
打开Grafana的配置页面,添加Prometheus的相关信息,测试确认对接正常
在Grafana里面添加Panel
数据源选取上一步配置好的Prometheus
添加两个监控Metric:
test_135_ifcounters_SAI_PORT_STAT_IN_CONFIGURED_DROP_REASONS_1_DROPPED_PKTS test_135_ifcounters_SAI_PORT_STAT_IN_CONFIGURED_DROP_REASONS_2_DROPPED_PKTS
发包验证
构造报文1,vlan_id为10,与Ethernet7所属VLAN不符,发入Ethernet7
构造报文2,vlan_id为60,但是dest_ip为交换机路由表中不存在的9.9.9.9,发入Ethernet7
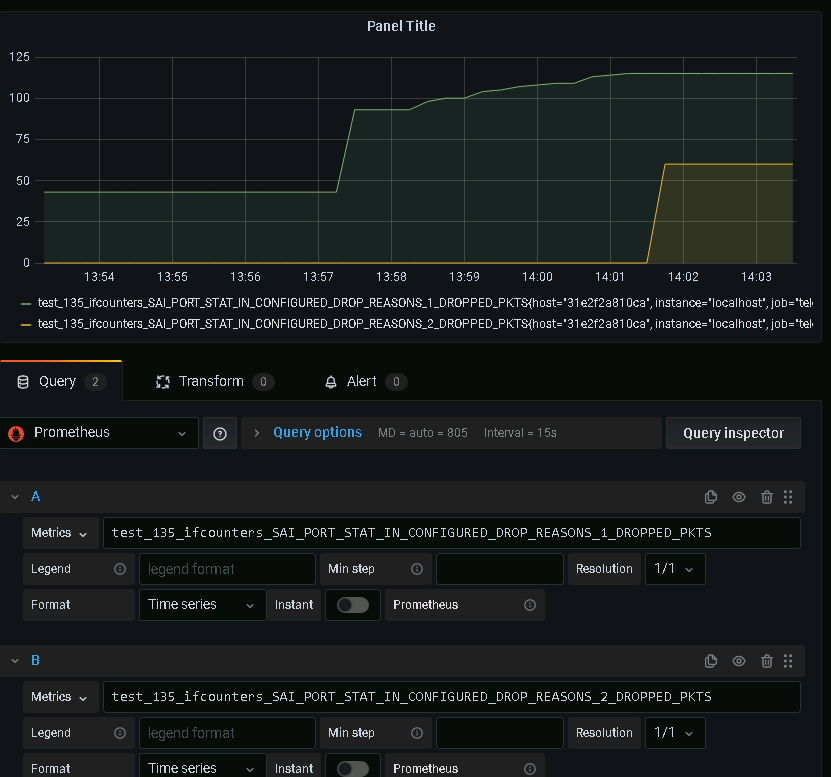
查看Panel页面,横坐标为时间轴,纵坐标为报文个数
图中绿色曲线代表进入Ethernet7的报文因为与入端口VLAN属性不符而被丢弃的报文个数变化
图中黄色曲线代表进入Ethernet7的报文因为查找不到相应的路由而被丢弃的报文个数变化
运维人员或者控制器可以基于上报的丢包统计消息快速排查故障位置,执行故障应对策略,恢复网络业务
编辑:黄飞
-
如何实现POE交换机串联?2025-03-25 1055
-
工业交换机的零延迟和零丢包2024-09-24 808
-
内网突发丢包率问题:华三交换机默认VLAN IP冲突2023-07-11 6105
-
网络交换机2023-04-28 1585
-
什么是网络交换机?网络交换机的分类标准2022-08-10 4187
-
项目中如何选择交换机?2021-01-12 1995
-
如何避免千兆以太网交换机能量数据控制丢包,有什么好的方法预防2021-01-11 2684
-
造成以太网交换机性能测试丢包的因素有哪些2020-12-08 5252
-
网络丢包常见故障分析及处理方式2020-12-01 2998
-
网络交换机的作用_网络交换机怎么用2020-04-02 7174
-
锐捷助互联网数据中心网络自动化、可视化运维2017-01-25 5486
-
网络交换机的应用类型2010-01-08 2875
-
基础知识:理解网络交换机的原理2009-04-13 3733
全部0条评论

快来发表一下你的评论吧 !

