

关于HCIA综合实验总结
描述
前言
本篇博客将对HCIA的所有内容做一个总结,整合为一个综合实验来完成。
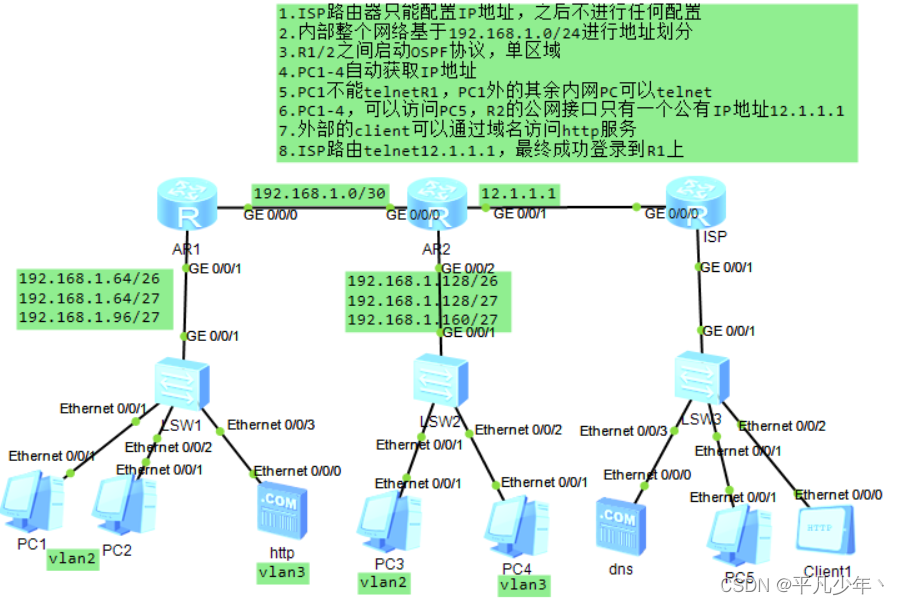
要求
1.ISP路由器只能配置IP地址,之后不进行任何配置 2.内部整个网络基于192.168.1.0/24进行地址划分 3.R1/2之间启动OSPF协议,单区域 4.PC1-4自动获取IP地址 5.PC1不能telnetR1,PC1外的其余内网PC可以telnet 6.PC1-4,可以访问PC5,R2的公网接口只有一个公有IP地址12.1.1.1 7.外部的client可以通过域名访问http服务 8.ISP路由telnet12.1.1.1,最终成功登录到R1上
一、子网划分
需要三个子网,将192.168.1.0/24 划分到 192.168.1.0/26
192.168.1.0/24 192.168.1.0/26 用于骨干网段 192.168.1.0/30 192.168.1.4/30 192.168.1.8/30 ...... 192.168.1.64/26 用于AR1虚拟网段 192.168.1.64/27 192.168.1.96/27 192.168.1.128/26 用于AR2虚拟网段 192.168.1.128/27 192.168.1.160/27 192.168.1.192/26
二、配置思路
1.IP地址 2.VLAN配置 3.DHCP服务 4.路由协议 5.ACL+NAT
三、配置命令
1.IP地址+vlan+dhcp服务
SW1
vlan batch 2 to 3 //创建vlan2-3 interface Ethernet0/0/1 //接口划入vlan port link-type access port default vlan 2 interface Ethernet0/0/2 port link-type access port default vlan 2 interface Ethernet0/0/3 port link-type access port default vlan 3 interface GigabitEthernet0/0/1 //Trunk干道 port link-type trunk port trunk allow-pass vlan 2 to 3
SW2
vlan batch 2 to 3 interface Ethernet0/0/1 port link-type access port default vlan 2 interface Ethernet0/0/2 port link-type access port default vlan 3 interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 2 to 3
R1
interface GigabitEthernet0/0/0 ip address 192.168.1.1 255.255.255.252 dhcp enable//开启dhcp服务 ip pool v2//创建IP地址池塘 gateway-list 192.168.1.65 network 192.168.1.64 mask 255.255.255.224 dns-list 114.114.114.114 8.8.8.8 ip pool v3 gateway-list 192.168.1.97 network 192.168.1.96 mask 255.255.255.224 dns-list 114.114.114.114 8.8.8.8 interface GigabitEthernet0/0/1.1//进入子接口(单臂路由) dot1q termination vid 2//服务vlan2 arp broadcast enable//开启ARP应答 ip address 192.168.1.65 255.255.255.224 dhcp select global//开启dhcp服务 interface GigabitEthernet0/0/1.2 dot1q termination vid 3 arp broadcast enable ip address 192.168.1.97 255.255.255.224 dhcp select global
R2
interface GigabitEthernet0/0/0 ip address 192.168.1.2 255.255.255.252 interface GigabitEthernet0/0/1 ip address 12.1.1.1 255.255.255.0 dhcp enable ip pool v2 gateway-list 192.168.1.129 network 192.168.1.128 mask 255.255.255.224 dns-list 114.114.114.114 8.8.8.8 ip pool v3 gateway-list 192.168.1.161 network 192.168.1.160 mask 255.255.255.224 dns-list 114.114.114.114 8.8.8.8 interface GigabitEthernet0/0/2.1 dot1q termination vid 2 ip address 192.168.1.129 255.255.255.224 arp broadcast enable dhcp select global interface GigabitEthernet0/0/2.2 dot1q termination vid 3 ip address 192.168.1.161 255.255.255.224 arp broadcast enable dhcp select global
ISP
interface GigabitEthernet0/0/0 ip address 12.1.1.2 255.255.255.0 interface GigabitEthernet0/0/1 ip address 3.3.3.1 255.255.255.0
2.OSPF配置
R1
ospf 1 router-id 1.1.1.1 //开启ospf协议,给定router-id area 0.0.0.0 //进入区域0 network 192.168.1.0 0.0.0.255 //宣告网段 interface GigabitEthernet0/0/0 ospf authentication-mode md5 1 cipher xiaoli123//在与邻居相连接口上做认证,保障安全
R2
ospf 1 router-id 2.2.2.2 default-route-advertise always area 0.0.0.0 network 192.168.1.0 0.0.0.255 interface GigabitEthernet0/0/0 ospf authentication-mode md5 1 cipher xiaoli123
3.ACL+NAT
R1
aaa local-user xiaoli password cipher xiaoli123//通过aaa创建账户 local-user xiaoli service-type telnet//账户对应的服务为telnet local-user xiaoli privilege level 15//账户权限1-15,15为最高等级 user-interface vty 0 4//用于telnet的接口 authentication-mode aaa//接口上调用账户 acl number 3000 //开启ACL 编号2000-2999为标准ACL,标准ACL只看源IP 3000-3999为扩展ACL rule 5 deny tcp source 192.168.1.94 0 destination 192.168.1.65 0 destination-port eq telnet//拒绝IP地址为192.168.1.94对192.168.1.65的telnet请求 rule 10 deny tcp source 192.168.1.94 0 destination 192.168.1.97 0 destination-port eq telnet rule 10 deny tcp source 192.168.1.94 0 destination 192.168.1.1 0 destination-port eq telnet interface GigabitEthernet0/0/1.1 traffic-filter inbound acl 3000 //接口上调用ACL
R2
acl number 2000 rule 5 permit source 192.168.1.0 0.0.0.255 //抓取来自192.168.1.0-255的流量,用于nat地址转换 interface GigabitEthernet0/0/1 nat outbound 2000 //在连接外网的接口上启用nat,1对多nat,用来访问外网 nat static protocol tcp global current-interface www inside 192.168.1.98 www netmask 255.255.255.255//1对1nat,用于固定某一服务所对应的IP地址 nat static protocol tcp global current-interface telnet inside 192.168.1.1 telnet netmask 255.255.255.255
4.服务器配置
http服务器
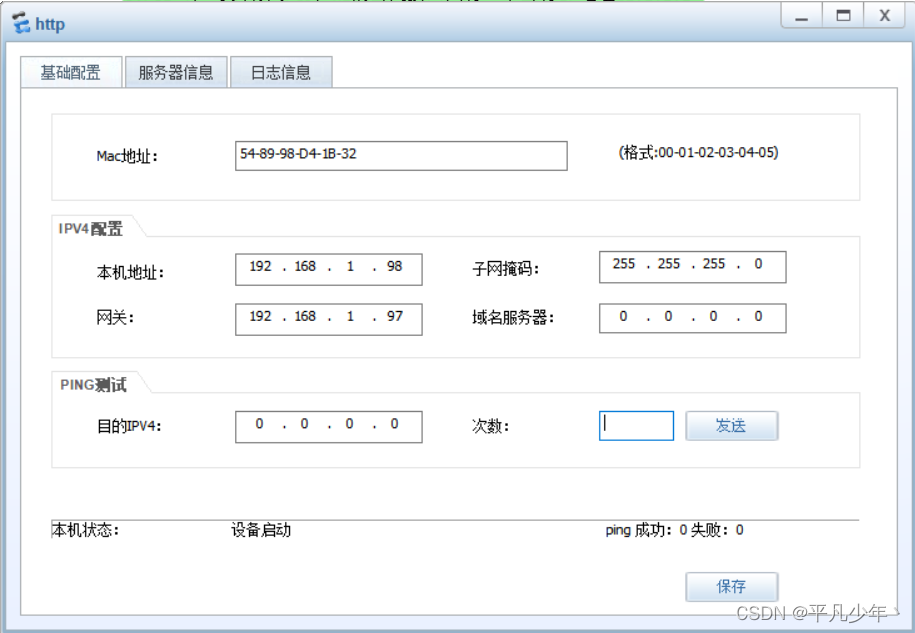
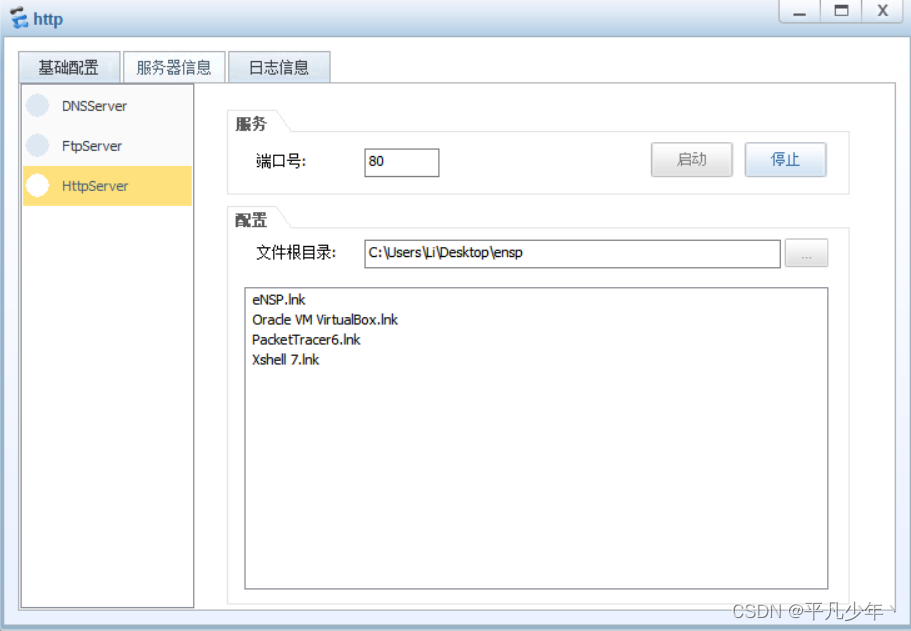
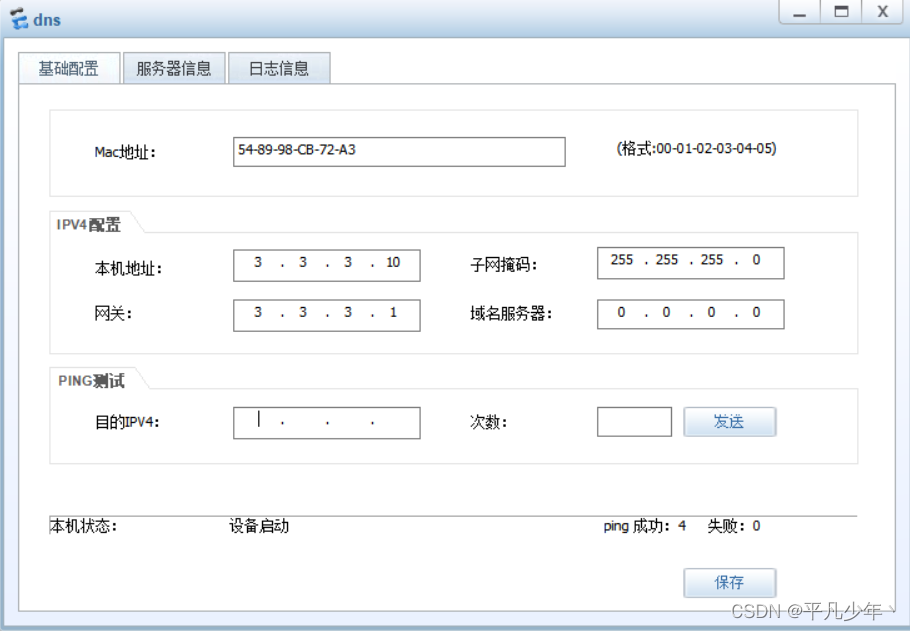
dns服务器
总结
到此,整个实验已经完成,如果可以顺利完成这个实验,说明你对HCIA的掌握很好。
审核编辑:黄飞
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。
举报投诉
-
关于C++模板总结2022-09-19 888
-
《单片机技术及原理》实验总结2021-11-23 1097
-
【实验】实验课总结2 实验一2021-11-21 461
-
直流无刷电机控制综合实验总结2021-09-22 1261
-
LabVIEW的ActiveX实验总结2021-08-04 1062
-
CCNA综合实验参考命令2021-05-11 553
-
请问将GSM模块实验加入到实验38综合实验需要添加一些什么文件?2019-04-08 1455
-
模拟电路实验--综合实验课件2017-02-07 777
-
信号与系统综合实验2016-12-17 733
-
认识综合布线系统实验2010-11-06 2865
-
小车综合控制实验2009-03-23 1388
-
分立器件综合设计实验2009-03-19 4663
-
ARM的综合实验2008-12-26 1419
-
Java综合练习实验2008-09-23 1318
全部0条评论

快来发表一下你的评论吧 !

