

[原创] Maxim DS28E83耐辐射安全认证器解决方案
应用案例
描述
Maxim公司的DS28E83是耐辐射安全认证器,从集成的非对称(ECC-P256)和对称(SHA-256安全函数推算核心密码工具,除了由硬件实现加密引擎的安全服务外,器件集成了FIPS兼容的真随机号码发生器(TRNG),10Kb安全OTP,一个可配置GPIO和一个唯一64位ROM身份码(ROM ID),医用灭菌抗性抗辐射高达75kGy (kiloGray),同时可使用户可编程制造或校准数据.1-Wire IO引脚±8kV HBM ESD保护,工作电压3.3V ±10%, 工作温度0℃ 到 +50℃ ,主要用在医疗安全认证,医疗工具/附件身份和校准,附件和外设安全认证,主控制器的密钥安全存储,固件和/或系统参数的安全引导或下载.本文介绍了DS28E83主要优势和特性,简化框图,典型应用电路图以及评估板DS28E83 EVK主要特性和电路图与材料清单.
The DS28E83 is a radiation-resistant secure authenticator that provides a core set of cryptographic tools derived from integrated asymmetric (ECC-P256) and symmetric (SHA-256) security functions. In addition to the security services provided by the hardware implemented crypto engines, the device integrates a FIPS-compatible true random number generator (TRNG), 10Kb of secured OTP, one configurable GPIO, and a unique 64-bit ROM identification number (ROM ID).
The ECC public/private key capabilities operate from the NIST defined P-256 curve and include FIPS 186-compliant ECDSA signature generation and verification to support a bidirectional asymmetric key authentication model. The SHA-256 secret key capabilities are compliant with FIPS 180 and are flexibly used either in conjunction with ECDSA operations or independently for multiple HMAC functions.
The GPIO pin can be operated under command control and include configurability supporting authenticated and nonauthenticated operation, including an ECDSA-based crypto-robust mode to support secure boot of a host processor.
DeepCover® embedded security solutions cloak sensitive data under multiple layers of advanced security to provide the most secure key storage possible. To protect against device-level security attacks, invasive and noninvasive countermeasures are implemented including active die shield, encrypted storage of keys, and algorithmic methods.
DS28E83主要优势和特性:
High Radiation Resistance Allows User-Programmable Manufacturing or Calibration Data Before Medical SterilizationResistant Up to 75kGy (kiloGray) of Radiation
One Time Programmable (OTP) 10kb of User Data, Keys, and Certificates
ECC-P256 Compute EngineFIPS 186 ECDSA P256 Signature and Verification
ECDH Key Exchange for Session Key Establishment
ECDSA Authenticated R/W of Configurable Memory
SHA-256 Compute EngineFIPS 180 MAC for Secure Download/Boot
FIPS 198 HMAC for Bidirectional Authentication and Optional GPIO Control
SHA-256 OTP (One-Time Pad) Encrypted R/W of Configurable Memory Through ECDH Established Key
One GPIO Pin with Optional Authentication ControlOpen-Drain, 4mA/0.4V
Optional SHA-256 or ECDSA Authenticated On/Off and State Read
Optional ECDSA Certificate to Set On/Off After Multiblock Hash for Secure Download
TRNG with NIST SP 800-90B Compliant Entropy Source with Function to Read Out
Optional Chip Generated Pr/Pu Key Pairs for ECC Operations or Secrets for SHA256 Functions
Unique and Unalterable Factory Programmed 64-Bit Identification Number (ROM ID)
Optional Input Data Component to Crypto and Key Operations
Advanced 1-Wire Protocol Minimizes Interface to Just Single Contact
Operating Range: 3.3V ±10%, 0℃ to +50℃
±8kV HBM ESD Protection of 1-Wire IO Pin
6-Pin, 3mm x 3mm TDFN
DS28E83应用:
Medical Consumables Secure Authentication
Medical Tools/Accessories Identification and Calibration
Accessory and Peripheral Secure Authentication
Secure Storage of Cryptographic Keys for Host Controllers
Secure Boot or Download of Firmware and/or System Parameters
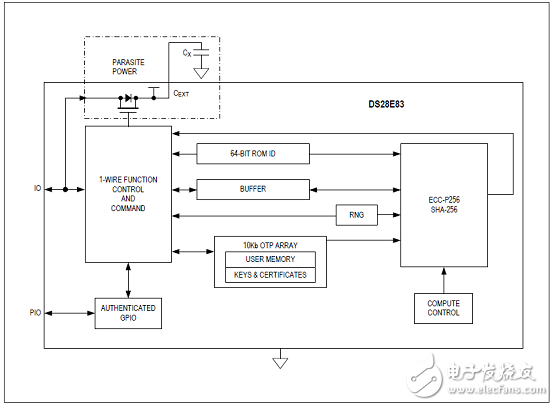
图1.DS28E83简化框图
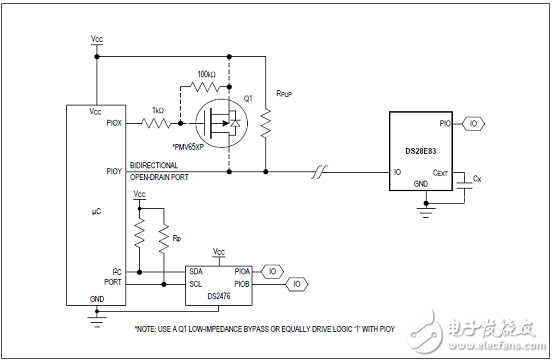
图2.DS28E83典型应用电路图
评估板DS28E83 EVK
The DS28E83 evaluation system (EV system) provides the hardware and software necessary to exercise the features of the DS28E83. The EV system consists of five DS28E83/ DS2476 devices in a 6-pin TDFN package, a DS9121AQ+ evaluation TDFN socket board, and a DS9481P-300# USB-to-I2C/1-Wire® adapter. The evaluation software runs under Windows® 10, Windows 8, and Windows 7 operating systems, both 64-bit and 32-bit versions. It provides a handy user interface to exercise the features of the DS28E83 and DS2476.
评估板DS28E83 EVK主要特性:
Demonstrates the Features of the DS28E83 DeepCover® Radiation Resistant 1-Wire Authenticator
Demonstrates the Features of the DS2476 DeepCover Secure Coprocessor
1-Wire/I2C Communication Is Logged to Aid Firmware Designers Understanding of DS28E83 and DS2476
1-Wire/I2C USB Adapter Creates a Virtual COM Port on Any PC
Fully Compliant with USB Specification v2.0
Software Runs on Windows 10, Windows 8, and Windows 7 for Both 64-Bit and 32-Bit Versions
3.3V ±3% 1-Wire Operating Voltage
Convenient On-Board Test Points, TDFN Socket
Evaluation Software Available by Request
评估板DS28E83 EVK包括:
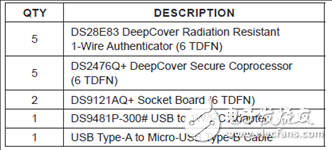
图3.DS28E83 EV评估系统外形图
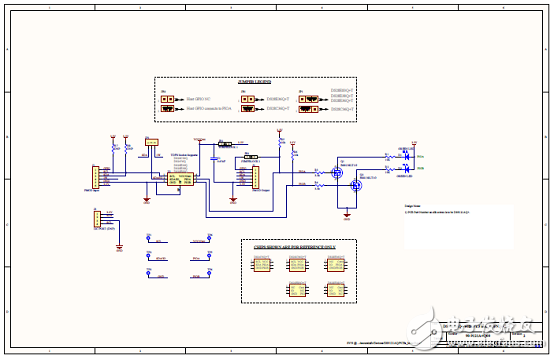
图4. DS28E83 EV评估系统电路图
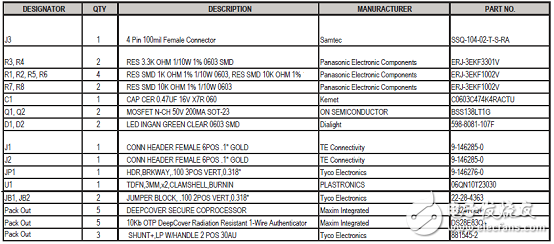
DS28E83 EV评估系统材料清单:
详情请见:
https://datasheets.maximintegrated.com/en/ds/DS28E83.pdf
和https://datasheets.maximintegrated.com/en/ds/DS28E83EVKIT.pdf
DS28E83.pdf
- 相关推荐
-
DS28E35 DeepCover安全认证器的特点及应用介绍2018-10-09 3988
-
Maxim Integrated推出DeepCover安全认证器件DS28E352013-06-18 1272
-
DS28EL25 DeepCover安全认证器 中文2013-08-23 1231
-
Maxim Integrated推出DeepCover安全认证器件2013-09-24 971
-
Maxim发布业界首款耐辐射安全认证器,可在恶劣环境下使用2018-07-14 3607
-
DS28E83 DeepCover防辐射1-Wire安全认证器简介2018-10-11 3486
-
DS28E38 DeepCover安全认证器为IoT设计提供更好的攻击措施2018-10-12 3056
-
DS28E38评估板的特点及ECDSA安全认证演示过程2018-10-08 5172
-
贸泽即日备货Maxim DS28E39和DS28E84 DeepCover认证器 为物联网节点添加保护层2019-07-31 899
-
无法克隆的安全IC DS28E382020-03-26 595
-
基于微控制器的DS28E40解决方案2021-01-18 2059
-
ADI推出DS28E30 1-Wire ECDSA安全认证器2022-05-27 1552
-
DS28E83Q+T DS28E83Q+T - (Maxim Integrated) - 专用 IC2022-11-16 72
-
DS28E83Q+U 专用 IC2022-11-18 64
-
DS28E07+ - (Maxim Integrated) - 存储器2023-07-31 98
全部0条评论

快来发表一下你的评论吧 !

