Cerbos 是一款云原生应用的访问控制工具,通过为应用程序资源编写上下文感知访问控制策略来增强授权控制。
- 使用直观的 YAML 配置语言编写访问规则
- 使用 Git-ops 基础架构来测试和部署
-
向 Cerbos PDP 发出简单的 API 请求,以评估策略并做出动态访问决策
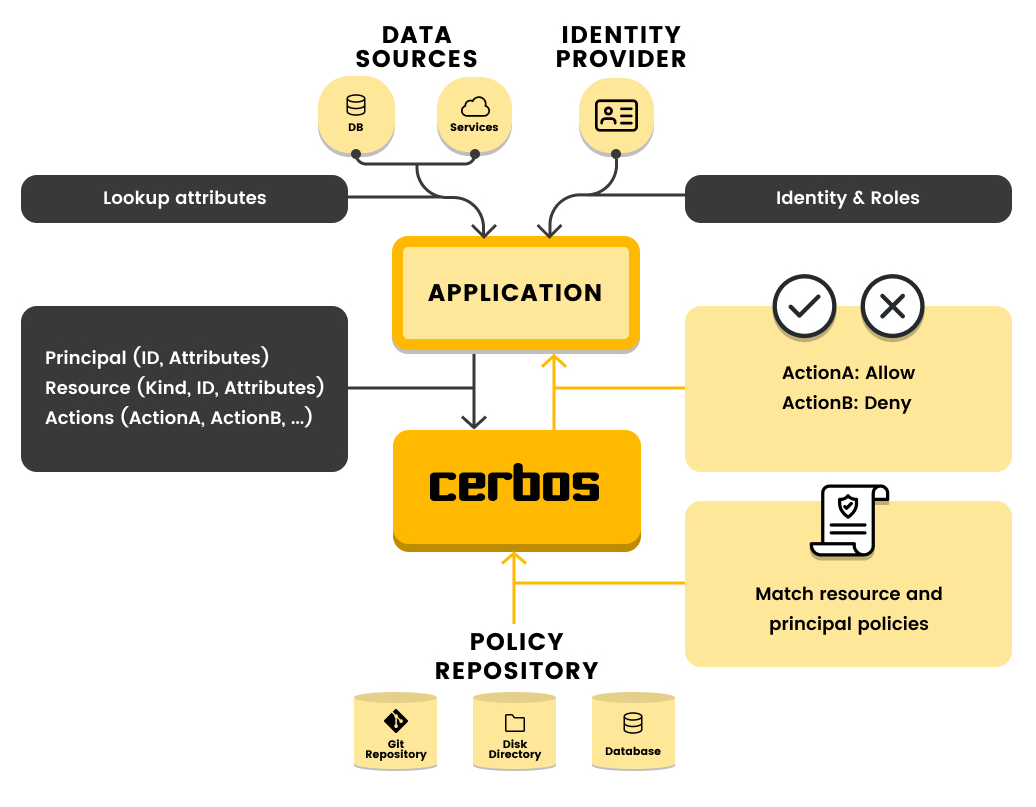
用例:
派生角色:根据上下文数据为用户动态分配新角色。
--- apiVersion: "api.cerbos.dev/v1" derivedRoles: name: common_roles definitions: - name: owner parentRoles: ["user"] condition: match: expr: request.resource.attr.owner == request.principal.id - name: abuse_moderator parentRoles: ["moderator"] condition: match: expr: request.resource.attr.flagged == true
资源策略:为资源编写访问规则。
--- apiVersion: api.cerbos.dev/v1 resourcePolicy: importDerivedRoles: - common_roles resource: "album:object" version: "default" rules: - actions: ['*'] effect: EFFECT_ALLOW derivedRoles: - owner - actions: ['view', 'flag'] effect: EFFECT_ALLOW roles: - user condition: match: expr: request.resource.attr.public == true - actions: ['view', 'delete'] effect: EFFECT_ALLOW derivedRoles: - abuse_moderator
API 请求
cat <<EOF | curl --silent "http://localhost:3592/api/check?pretty" -d @- { "requestId": "test01", "actions": ["view"], "resource": { "kind": "album:object", "instances": { "XX125": { "attr": { "owner": "alicia", "id": "XX125", "public": false, "flagged": false } } } }, "principal": { "id": "alicia", "roles": ["user"] } } EOF
API 响应
{
"requestId": "test01",
"resourceInstances": {
"XX125": {
"actions": {
"view": "EFFECT_ALLOW"
}
}
}
}







