
资料下载

该解决方案中的simpler硬化物联网安全的Wi - Fi的连接设计
该解决方案中的simpler硬化物联网安全的Wi - Fi的连接设计
Wi-Fi连接是许多物联网设备的关键要求和黑客最喜爱的目标。弱安全实现使设备在正在进行的网络通信中渗透。更糟的是,物联网设备可以在其生命周期早期遭受攻击时,该设备试图加入受信任的网络。
使用从德克萨斯仪器的双核无线微控制器,工程师可以很容易硬化安全物联网设备在整个产品生命周期,并支持多层终端到终端的安全策略。
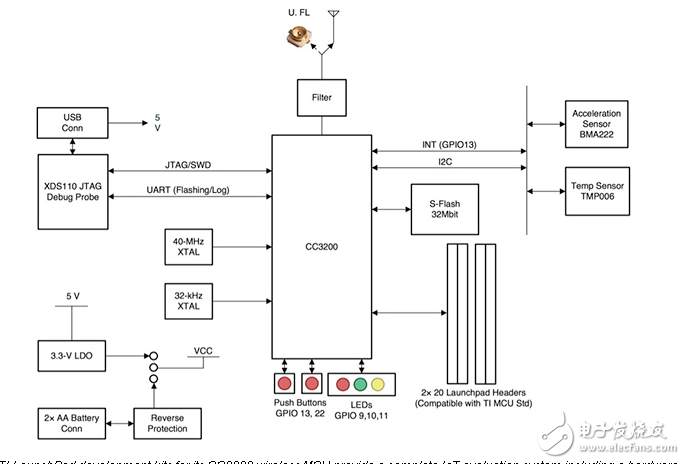
Security components
Security in any system requires a multilayered approach. Although data encryption often gains the most attention among security measures, it is only one aspect of a robust security policy. Black-hat methods such as man-in-the-middle attacks exploit any weakness well before encrypted data exchange begins. Indeed, secure hosts authenticate clients to ensure that only authorized users, devices, or other systems gain access. Conversely, those clients authenticate the host to verify its identity.
This kind of mutual authentication lies at the heart of secure applications, but it ultimately relies on more fundamental mechanisms and policies. Foremost among these, secret keys and an established root of trust are the building blocks of any secure application. In the kind of public key infrastructure (PKI) typically used on the Internet, public keys paired with secret private keys provide essential validation of an entity’s identity. The X.509 certificate standard wraps the entity’s public key in a broader context that documents that identity, building on a chain of certificates to provide a solidly grounded root of trust for the application.
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。 举报投诉
- 相关下载
- 相关文章






