
资料下载

Strengthening the Weakest Link
Strengthening the Weakest Link
“物联网”构成了物联网需要高效的安全技术,可以防止篡改,使设备进行身份验证,从而防止未经授权的访问网络。
在物联网(物联网)的应用程序是容易受到黑客攻击在多个地点,如端点和网络集中器,网络接口,移动应用程序和云服务。黑客的意图是一样的物联网本身的多样性,并可能范围从报告的能源使用情况下的公用事业提供商,窃取数据,如密码或财务信息,或更严重的行为,如工业破坏或国际恐怖主义。
正如活动,如在线商务需要改进的安全性,为用户提供保证,他们的财务数据受到保护,物联网世界也来了解非常真实的安全风险,目前。
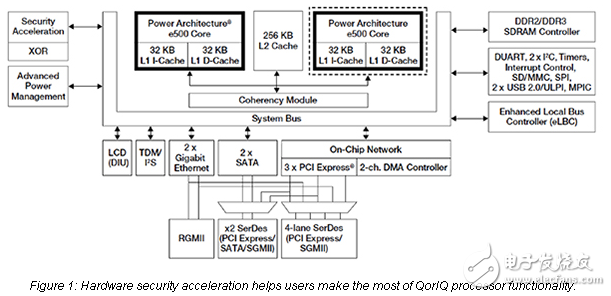
The IoT Security Learning Curve
Connecting small computerized devices such as smart appliances, smart energy meters or industrial SCADA systems to a network has highlighted many advantages compared with traditional scenarios in which equipment has not been interconnected or has been deployed in closed networks using proprietary or specialized communication protocols. Widespread connectivity using industry-standard protocols such as IP, often over Ethernet or over wireless links like Bluetooth® or ZigBee®, allows easier control and reporting as well as new features such as remote monitoring and control via a mobile device.
On the other hand, extending connectivity presents opportunities for hackers to gain unauthorized access. IoT devices such as mobiles, wearables, and smart devices installed in customer premises or publicly accessible areas are vulnerable to physical tampering in addition to unauthorized access via a network connection.
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。 举报投诉
- 相关下载
- 相关文章







