
资料下载

对于一个老于世故的物联网硬件的安全
对于一个老于世故的物联网硬件的安全
即使是最小的设备在互联网上的黑客试图窃取信息,潜在的目标,伪造数据,或破坏或禁用设备本身。在互联网上开发的可信计算原理现在正在为物联网提供低成本、低功耗的基于硬件的安全。
互联网的破解的东西
各种组织正变得热衷于利用物联网来简化活动,降低成本,提高盈利能力。微小,低成本,低功耗智能“东西”可以很容易地连接到互联网,开放的可能性,这是根本无法抗拒的工程师被迫探索新的技术途径,也为业务经理看到机会,以增加销售和改善运营。消费者也被“酷”的因素所吸引,用遥控产品控制移动设备,以及减少家庭账单的机会。
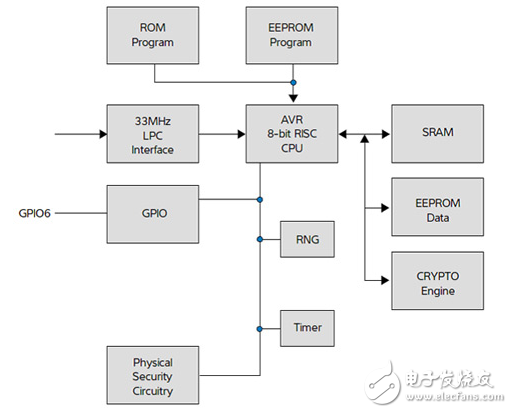
In the excitement, however, one key issue may have been overlooked. Security can be a low priority for developers rushing to create advanced new products and roll them out to customers, and is also likely not be a core skill. As far as IoT applications are concerned, it can be difficult to identify the interest a hacker may have in gaining access to a device. However, establishing a connection is easy, and if the device is not properly secured a hacker can gain valuable information such as user passwords simply by observing data flows.
Researchers at Symantec have carried out experiments by intercepting Bluetooth® transmissions between the fitness trackers and smartphones of passers-by in public places. The data intercepted contained un-encoded passwords used to connect the wearers’ devices. Given that many people use the same password for multiple logins, this information in the hands of a hacker can leave important assets vulnerable to unauthorized access, such as financial accounts or personal data kept in the cloud.
声明:本文内容及配图由入驻作者撰写或者入驻合作网站授权转载。文章观点仅代表作者本人,不代表电子发烧友网立场。文章及其配图仅供工程师学习之用,如有内容侵权或者其他违规问题,请联系本站处理。 举报投诉
- 相关下载
- 相关文章






